.jpg?sfvrsn=ddb02773_4) What is this Open Systems Interconnection Reference Model (OSI/RM) thing, and why should I care? I must admit, that was my first reaction when I started to learn about how devices are networked together. At first, memorizing the OSI/RM seemed to be another overly theoretical, academic exercise to me. But once I started troubleshooting network connections, implementing security controls and using emerging tech, I quickly found it absolutely essential to any IT pro’s career. This is because the OSI/RM ensures all of the hardware, applications and protocols from myriad vendors can work and play well together.
What is this Open Systems Interconnection Reference Model (OSI/RM) thing, and why should I care? I must admit, that was my first reaction when I started to learn about how devices are networked together. At first, memorizing the OSI/RM seemed to be another overly theoretical, academic exercise to me. But once I started troubleshooting network connections, implementing security controls and using emerging tech, I quickly found it absolutely essential to any IT pro’s career. This is because the OSI/RM ensures all of the hardware, applications and protocols from myriad vendors can work and play well together.
What Is the OSI/RM?
The OSI/RM, shown below, is a seven-layer framework that the International Organization for Standardization created in 1980, thanks to the work of a committee of experts led by Hubert Zimmerman. You can purchase and read the original article on the IEEE website, if you want.
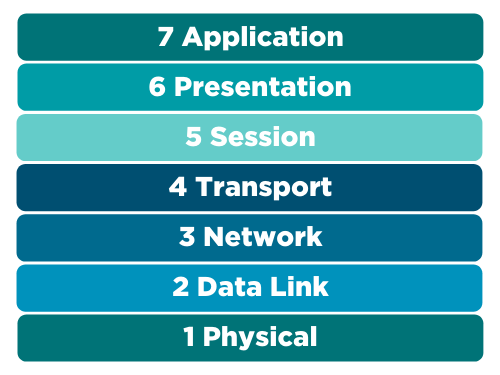
Figure 1: The seven layers of the OSI/RM
The OSI/RM describes the universal packetization process. That’s a fancy way of saying that it describes the steps any device follows when it wants to share data with another device.
Why Seven Layers?
Each layer of the OSI/RM describes seven functions that have to occur when one device wants to send data to another successfully. When two computers talk to each other, they do so by creating and exchanging packets. Each time you use your mobile phone to send a message to someone via a cloud resource, such as Slack or LinkedIn, that data starts the packetization process at the application layer (also known as layer 7). Each layer has specific responsibilities, as shown below.
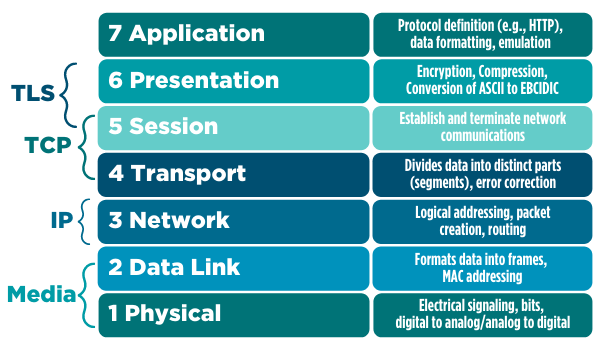
Figure 2: Mapping protocols and procedures to the OSI/RM
To put data on the network, your device processes that data has to be handled appropriately by each layer. This is why you will often hear terms like down the stack and up the stack when it comes to networking.
Also, notice that the OSI/RM helps describe common protocols and functions. Transport layer security (TLS) is the standard way that web browsers and other tools encrypt transmissions. Using the OSI/RM, you can see that TLS is enabled at layers 5 and 6. If you’ve heard of the transmission control protocol (TCP) and the internet protocol (IP), you can see how these two intertwined protocols map to layers 3, 4 and 5 of the OSI/RM. If you’ve ever seen a media access control (MAC) address, now you know that layer 2 is largely responsible for managing all processes associated with it.
OSI/RM and Headers
As your mobile phone begins the process of sending that message to your friend, your phone adds a header for each layer of the OSI/RM. You’ve likely heard of terms like segment, packet and frame. As shown below, each of these terms describes the results of the packetization process.
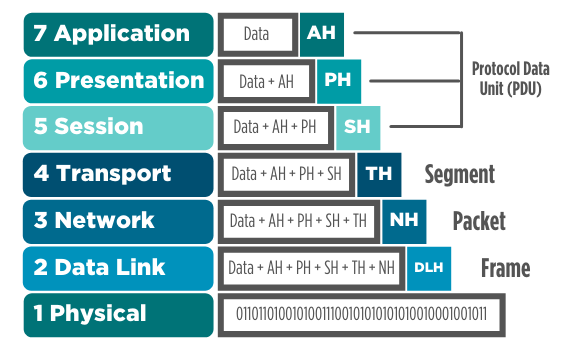
Figure 3: How the OSI/RM is used to model the creation of network packets
When your computer is finished processing the data you want to send, this data is neatly encapsulated in six headers, and then placed on a wired or wireless network as a stream of bits (e.g., 011101001). The physical layer doesn’t add a header; it describes the process of creating the actual network bitstream.
When the cloud service you’re using receives that data, it then reverses the packetization process, removing each header. The figure below summarizes how your mobile phone would first create a packet, then send it across a network. The cloud resource (e.g., Slack or LinkedIn) then removes each packet header to read the data you sent.
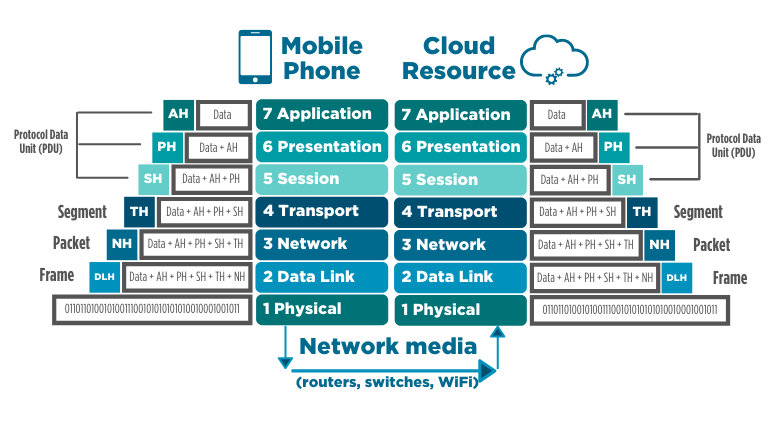
Figure 4: Two computers communicating, as shown by the OSI/RM to get to the data
The receiving computer, in this case, the cloud resource, needs to remove each header to get to your data. Each time you send a message using LinkedIn to your friend via WiFi, you’re repeating this process an almost infinite number of times.
I often compare this process to a Russian nesting doll. Those are the dolls that are placed inside of each other – each one gets smaller and smaller.
Let me explain what I mean by nesting during the packet creation process. Below, you can see the simple Wireshark packet capture of a movie that I was watching the other day. I’ve highlighted a specific packet in black.
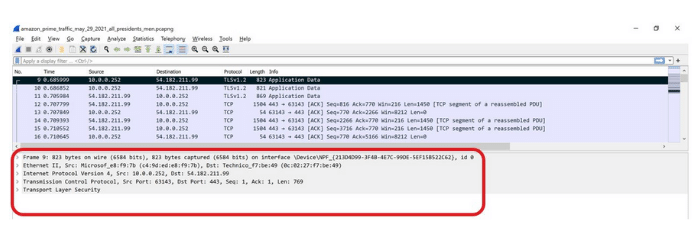
Figure 5: Viewing the contents of a packet in Wireshark
Take a closer look at the bottom of the image I’ve highlighted in red. Notice that this packet capture shows the frame, the networking layer (e.g., IP), the session information (e.g., TCP segment, with source and destination ports), the media/Ethernet information (complete with MAC addresses) and encryption (TLS). It’s no coincidence that Wireshark represents packets in the exact same layers of the OSI/RM. After all, the developers who created TCP/IP, Wireshark and the streaming service all follow that model.
Why the OSI/RM Is Essential
The OSI/RM is critical to learn because like all standards, it:
- Is openly available: Developers and manufacturers refer to it constantly as they create new devices and applications.
- Improves communication: It provides a “lingua franca” that allows us all to communicate clearly. This helps create consensus, as well.
- Sets the stage for better troubleshooting: It provides perspective that allows you to ask just the right questions as you strive to isolate a particular networking problem.
- Empowers people to understand new tech: When the OSI/RM was first created, the client/server model that created Microsoft had barely even been born. It was still a pretty mainframe-centric world then. Routers existed, but switches hadn’t been invented. Firewalls were rarely used. But folks who knew the OSI/RM could easily adapt and learn new things, because they had the perfect framework. Similarly, when I first learned networking and security back in the mid to late 1990s, the cloud and the Internet of Things really weren’t known commodities. But, once I heard about them, I easily folded them in to my brain, thanks to the OSI/RM.
Learning More About the OSI/RM
Here are a few resources that can help you learn more about the OSI/RM:
- CompTIA CertMaster Learn for A+
- Understanding Network Data Delivery: Layers 2 and 3 of the OSI Model
- The OSI Model Explained and How to Easily Remember its 7 Layers
Over the years, people have used various mnemonic devices to learn each layer, usually starting from the physical layer on up to the application layer.
These include:
- People Don’t Need Those Stupid Packets Anyway
- Please Do Not Teach Students Pointless Acronyms
- Please Do Not Throw Salami Pizza Away
- Please Do Not Throw Sausage Pizza Away
Choose your own method. I learned it by opening up a packet capture and getting some practical lab experience.
Thank Goodness for the OSI/RM!
Understanding the OSI/RM does more than just help me comprehend networking at an abstract level; it helps me troubleshoot. For example, when I am working with routers, I’m usually working at layer 3. When discussing firewalls, I often think in terms of layers 3, 4 and 5. If it’s time to talk about virtual LAN (VLAN) settings, then I’m thinking in terms of layer 2, and so forth.
Learning the OSI/RM helps me keep pace with innovation. As I transitioned from a largely client/server mindset into the cloud, I used the trusty OSI/RM to provide context. The OSI/RM also helps me discuss important security procedures with fellow professionals. As you move forward in your career, you’ll be glad it exists, and even more glad that you have learned it.
CompTIA is here to support you throughout your IT career. Get free resources, career advice, and special offers on CompTIA training and certifications!

