The Path To Secure Remote Network Connectivity Goes Through Company-Issued Routers: Aberdeen Research
IT Toolbox
JUNE 22, 2023
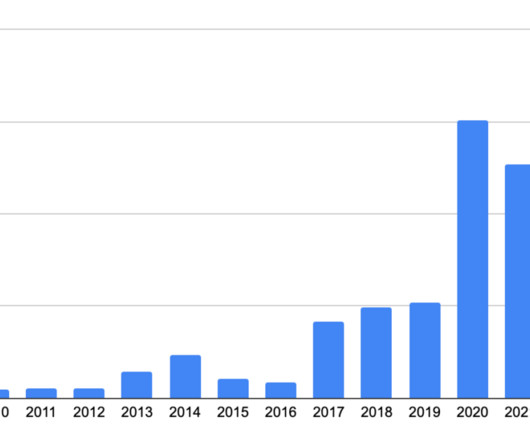
Organizations that assign a managed, company-secured router can reduce security risks by four times. The post The Path To Secure Remote Network Connectivity Goes Through Company-Issued Routers: Aberdeen Research appeared first on Spiceworks.










































Let's personalize your content