Why it matters: There's a joke that's been circulating in the security community that Intel CPUs have more holes than Swiss cheese, and new research published this month doesn't help the company shake off that reputation. A newly-discovered side-channel attack is less effective on Chipzilla's recent CPUs, but it serves as a reminder that speculative execution flaws are difficult to fix.
Researchers at the University of Maryland, Tsinghua University, and the Beijing University of Posts and Telecommunications recently published an interesting paper detailing a new side-channel attack on Intel processors that is quite different from other vulnerabilities exposed in the past.
The new flaw can be exploited as a side-channel of Meltdown, which leads to a 100 percent success rate against processors like the Core i7-6700, Core i7-7700, and Core i9-10980XE. For those of you unfamiliar with Meltdown, it was a collection of exploits for a critical vulnerability in the way modern processors perform something called "speculative execution" to achieve moderate performance gains in certain scenarios.
While Meltdown has been mostly mitigated at the OS, firmware, and hardware levels, the problem is too hard to fully fix and as such has persisted to this day. In the case of this new side-channel attack, it doesn't rely on the cache system and the setup doesn't require resetting the EFLAGS register so researchers believe it will be much harder to mitigate.
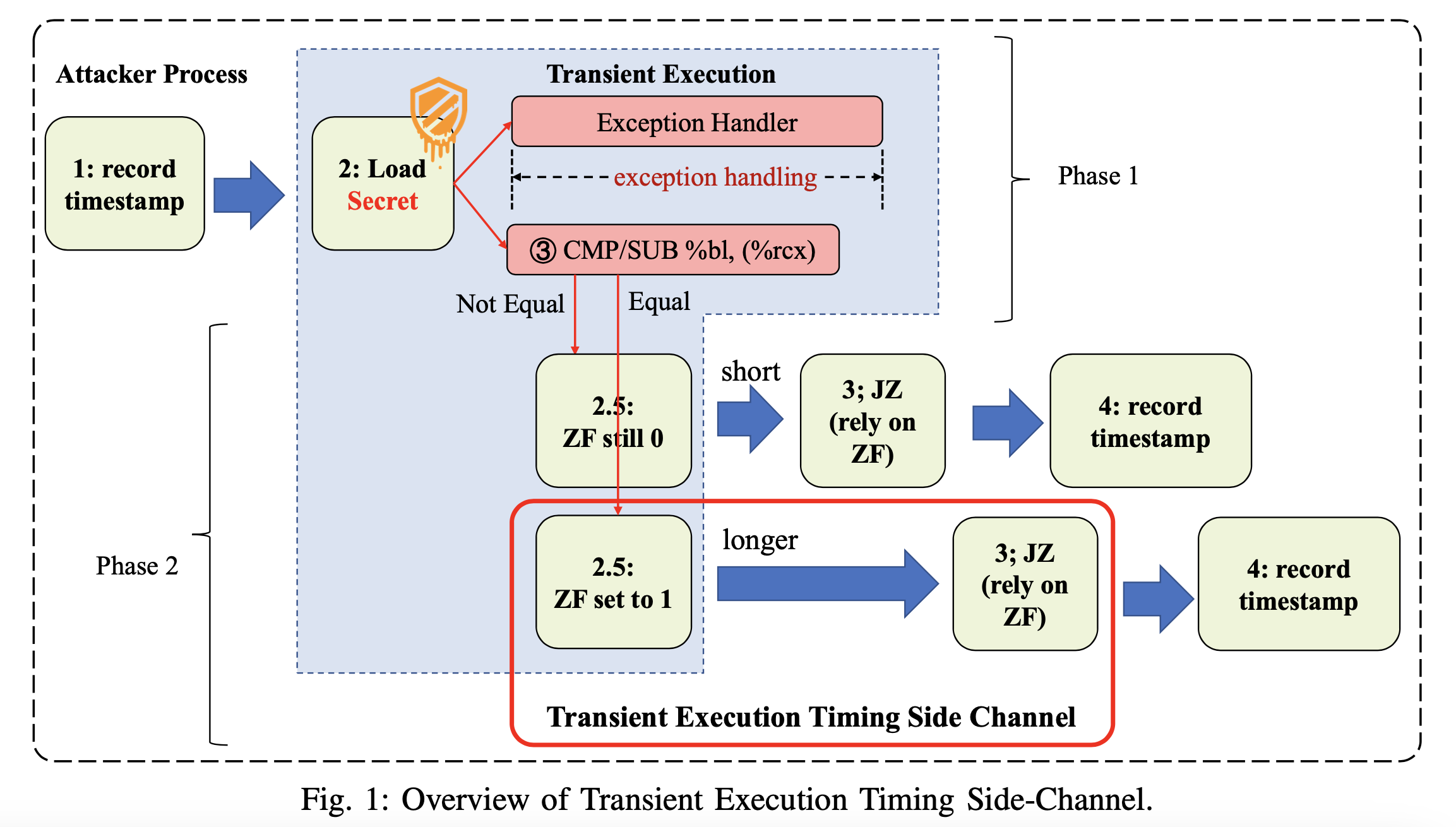
The EFLAGS register is used to describe the current status of CPU operations with several flags that are set to either 1 or 0. Researchers discovered they could exploit the way this works in Intel CPUs, where a change in the EFLAGS register in transient execution can make some "jump on condition code" (Jcc) instructions execute slightly slower.
First, they encode secret data into the EFLAGS register and then measure the execution time of the Jcc instruction context to decode said data. The root cause of this vulnerability is still a mystery, but researchers suspect Intel uses a buffer in the execution unit of its CPUs that needs time to revert whenever the execution should be withdrawn, and this in turn could cause a stall if the next instruction depends on the target of said buffer.
The good news is that this attack is somewhat less effective against newer chips (Intel 11th-gen and above) where a hacker would need to repeat it thousands of times to achieve the same effect. Furthermore, Intel's new 13th-gen vPro processors come with more security management features that give organizations better prevention and detection capabilities against side-channel attacks.
Researchers note in their paper that it's possible to mitigate their transient execution timing attack, but they aren't easy to implement as they require significant changes to how the Jcc instructions work and assembly code optimizations.
Image credit: Daniel Pantu