In this post, you will learn to block Potentially Unwanted Applications in Windows. The potentially unwanted application (PUA) protection feature in Microsoft Defender Antivirus can detect and block PUA on endpoints in your network.
Potentially unwanted applications aren’t considered viruses or malware, but these apps might perform actions on endpoints that adversely affect endpoint performance or use. PUA can also refer to applications that are deemed to have poor reputations.
Microsoft Defender SmartScreen determines whether a site is potentially malicious by analyzing visited web pages and looking for indications of suspicious behavior.
SmartScreen also helps us whether a downloaded app or app installer is potentially malicious by checking downloaded files against a list of reported malicious software sites and programs known to be unsafe.
Windows Security has reputation-based protection that can help protect your PC from potentially unwanted applications. There are other security features in Reputation-based protection settings, such as SmartScreen of Microsoft Edge and Microsoft Store Apps, that protect against phishing and downloading malicious files.
- Best Antivirus for Windows 11 Microsoft Defender | App Browser Protection | Firewall Protection
- Check Firewall Port is Open or Block on Windows 11 using PowerShell Command
- Install Microsoft Windows Defender Application Guard for Edge
Block Potentially Unwanted Applications in Windows | Microsoft Defender
Let’s follow the steps to turn on Microsoft Reputation-based protection, and You must be signed in as an administrator.
- On your Windows 10 or Windows 11 device, Click on the Start button.
- Type Windows Security in the search box. Click on App & browser control directly from search results OR Open Windows Security, and click on App & browser control.
- Click on the Reputation-based protection settings. If UAC prompts you, select Yes to continue.
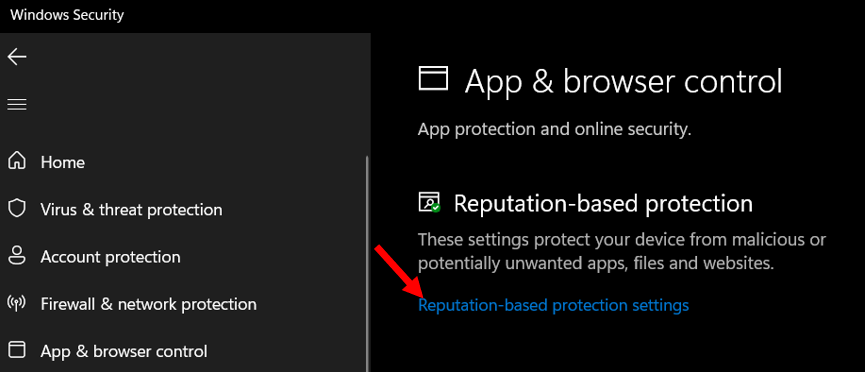
Here you manage the setting to protect your device from malicious or potentially unwanted apps, files, and websites. These settings are available for different categories –
- Check apps and files – Turn On
- SmartScreen for Microsoft Edge – Turn On
- Potentially unwanted app blocking – Turn On
- SmartScreen for Microsoft Store Apps – Turn On
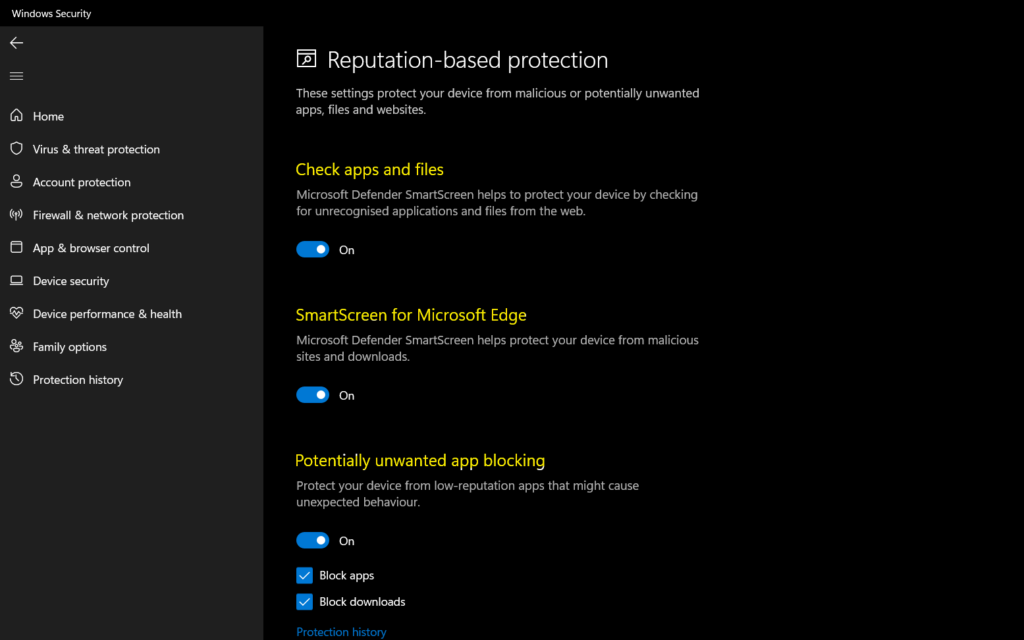
You’ll find a control that lets you turn potentially unwanted app blocking off and select if you want to block apps, downloads, or both.
It’s recommended that you leave this feature on and enable both block apps and block downloads.
- Block apps will detect PUA that you’ve already downloaded or installed, so if you’re using a different browser, Windows Security can still detect PUA after you’ve downloaded it.
- Block downloads look for PUA as it’s being downloaded, but it only works with the new Microsoft Edge browser.
Enable Potentially Unwanted Applications PUA Using PowerShell
You could run the following PowerShell command from Windows Terminal or Terminal application to enable PUA protection.
Copy and Paste the following command to install this package using PowerShellGet –
Install-Script -Name WindowsDefender_InternalEvaluationSettingsYou can also enable many protection capabilities of Windows Defender Antivirus using the following command.
"Enable real-time monitoring"
Set-MpPreference -DisableRealtimeMonitoring 0
"Enable cloud-deliveredprotection"
Set-MpPreference -MAPSReporting Advanced
"Enable sample submission"
Set-MpPreference -SubmitSamplesConsent Always
"Enable checking signatures before scanning"
Set-MpPreference -CheckForSignaturesBeforeRunningScan 1
"Enable behavior monitoring"
Set-MpPreference -DisableBehaviorMonitoring 0
"Enable IOAV protection"
Set-MpPreference -DisableIOAVProtection 0
"Enable script scanning"
Set-MpPreference -DisableScriptScanning 0
"Enable removable drive scanning"
Set-MpPreference -DisableRemovableDriveScanning 0
"Enable Block at first sight"
Set-MpPreference -DisableBlockAtFirstSeen 0
"Enable potentially unwanted apps"
Set-MpPreference -PUAProtection Enabled
"Schedule signature updates every 8 hours"
Set-MpPreference -SignatureUpdateInterval 8
"Enable archive scanning"
Set-MpPreference -DisableArchiveScanning 0
"Enable email scanning"
Set-MpPreference -DisableEmailScanning 0
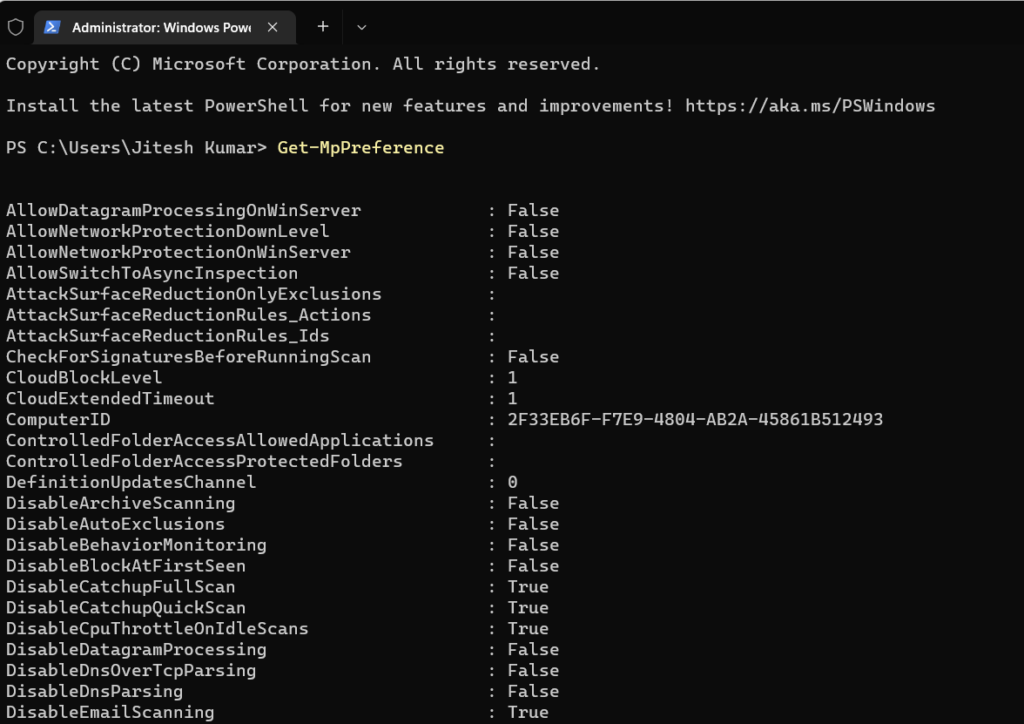
To display current Windows Defender settings, you can use the cmdlet Get-MpPreference to display the status. Scroll down the results and look for the value PUAProtection : 1 indicates that PUA Protection is enabled.
Potentially Unwanted Applications – Scenario
You can follow the steps to test the scenarios based on Microsoft recommendations –
- Go to http://www.amtso.org/feature-settings-check-potentially-unwanted-applications/
- Click the “Download the Potentially Unwanted Application ‘test’ file” link.
- After downloading the file, it is automatically blocked and prevented from running.
Important – If you are able to download this file successfully, your anti-malware solution is NOT configured correctly to detect Potentially Unwanted Applications, or DOES NOT conform to industry best practices.
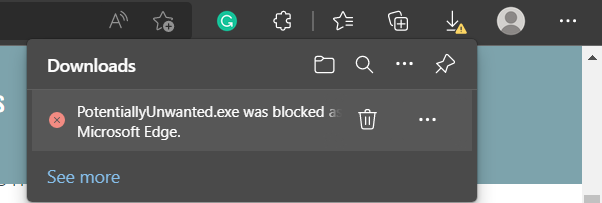
When Microsoft Edge detects a PUA, you will see a message when downloading a potentially unwanted app. Here is what users will know when the feature blocks a download.
Users can choose to keep it by tapping … in the bottom bar, choosing to Keep, and then choosing to Keep anyway in the dialog that appears.
When is PUA Detected?
When Windows Security detects a potentially unwanted app, you’ll get an App & Browser control notification indicating that a potentially unwanted app has been found.
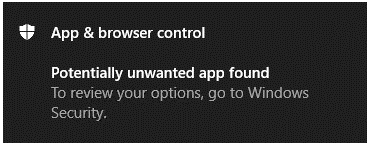
Click on the notification to go to the Virus & threat protection area of Windows Security, then click on the name of the PUA to select the action to take.
Configure PUA Protection Using Intune
You can manage Microsoft Defender policies with Microsoft Endpoint Manager Intune. There are different ways to manage a Defender policy. The preferred and easiest method (using a security baseline template) for smaller organizations is explained in the following post.
Read More – Intune Security Baseline Microsoft Defender Policy Troubleshooting Tips
Another method in Intune called Settings catalog policies is to configure Microsoft Defender policies. You can read more about Configure Microsoft Defender SmartScreen Using Intune.
This post about Configure Potentially Unwanted Applications PUA Protection in Microsoft Edge will help you assign the policy set up protection by enabling the potentially unwanted apps to feature in Microsoft Edge using Intune setting catalog policies.

