A little over three months after the Maze ransomware group announced it would be closing its operations, the master decryption keys have been released by the alleged malware developer.
Maze gained notoriety in 2019 for stealing data from organizations and demanding ransom for the data to be returned. This made Maze unique as the operators encrypted files on a corporate network with ransomware, making them inaccessible, and also extracted the data and threatened to make the data public if the ransom was not paid—double extortion.
After announcing Maze ransomware would shutdown, the group rebranded as Egregor. But this new group didn't last very long after some members were arrested in Ukraine in late 2021.
Now, the decryption keys for the malware have been leaked in Bleeping Computer forums by a user known as "Topleak," who claims to be a developer of the ransomware.
Ransomware dev leaks decryption keys
In the forum, Topleak says that this was a planned leak and unrelated to recent efforts from law enforcement that led to arrests of several cybercriminals. Topleak also noted that none of the team members will return to this type of malicious cyber activity.
You can see a screenshot of his post below:
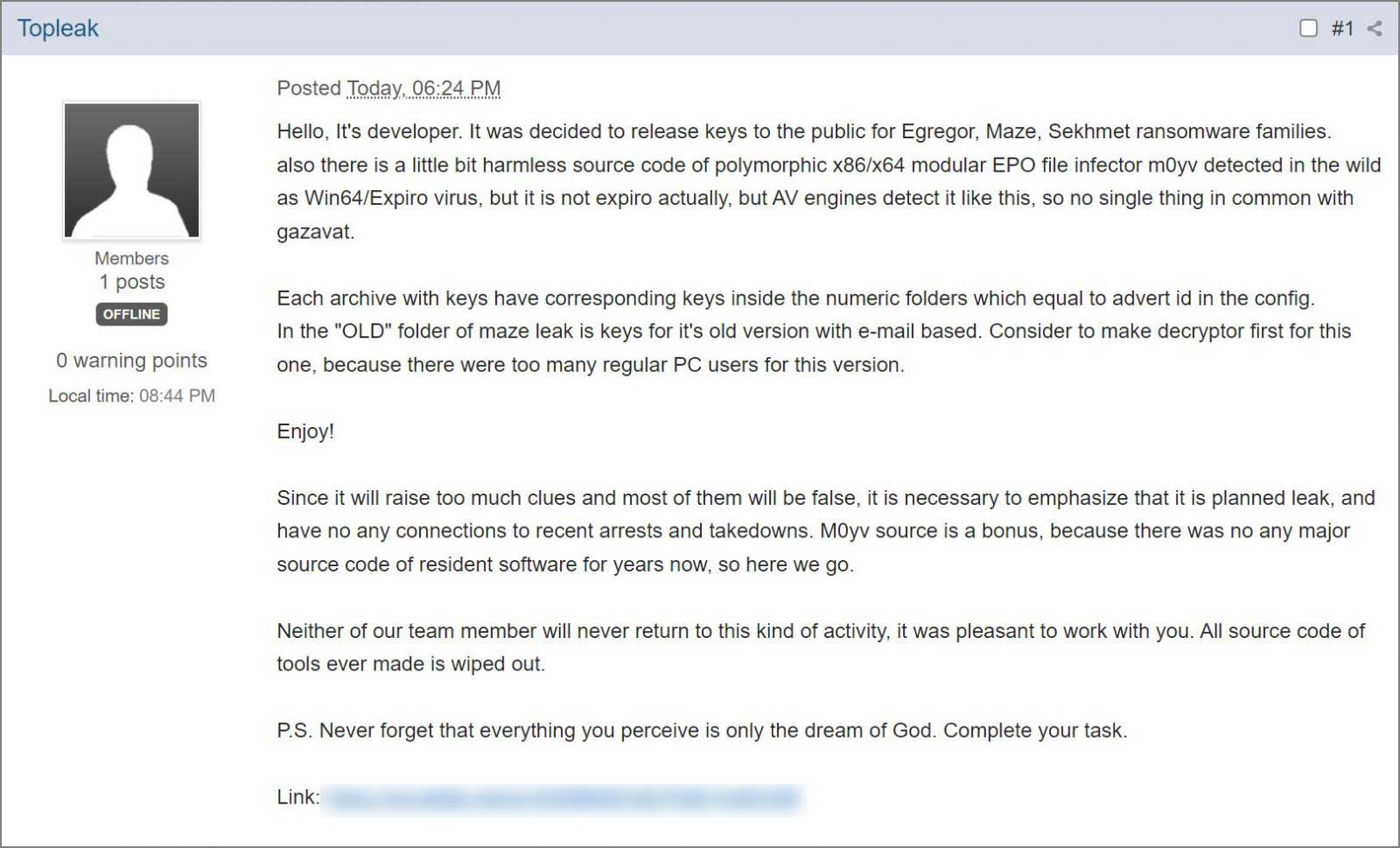
According to Bleeping Computer, the post included a link to a 7-Zip file with four archives containing the decryption keys, as well as the source code for a "M0yv" malware used by the ransomware gang:
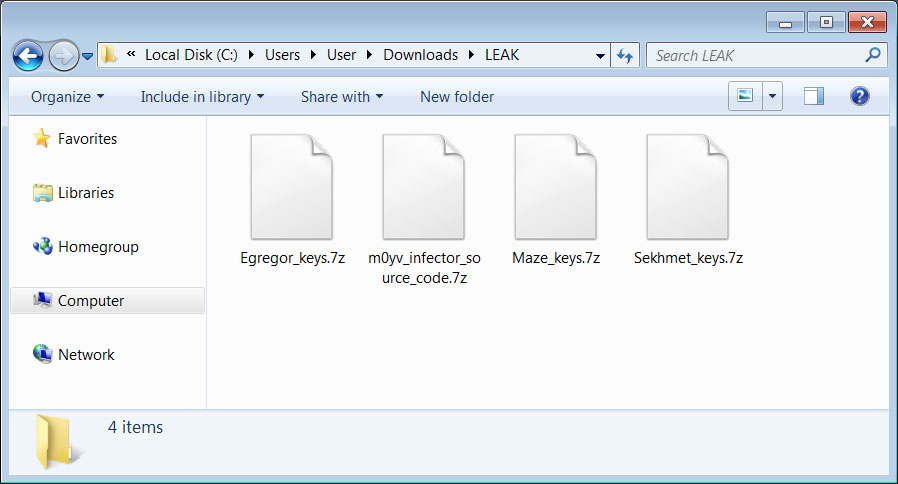
Each of these files "contains the public master encryption key and the private master decryption key associated with a specific 'advert', or affiliate of the ransomware operation."
Here is the total number of keys released for each operation:
- Maze: Nine master decryption keys for the original malware that targeted non-corporate users
- Maze: 30 master decryption keys
- Egregor: 19 master decryption keys
- Sekhmet: One master decryption key
Following this forum post, Emsisoft released a decryptor to allow any Maze, Egregor, and Sekhmet victims who have been waiting to recover their files for free.
For more information on the decryption keys for the Maze and Egregor ransomware operations, see the original story from Bleeping Computer.





