In today's digital world, automation is becoming increasingly widespread, giving rise to the prominence of bots. Bots are highly versatile software programs designed to automate tasks and streamline processes. While they offer convenience and efficiency, we must recognize the potential for misuse.
Over the past few years, bots have emerged as a new cybersecurity threat, as they can be manipulated for malicious purposes. This article will explore the realm of malicious bots, uncover their cybersecurity risks, and provide valuable insights on safeguarding yourself from bot attacks.
Stats on bots
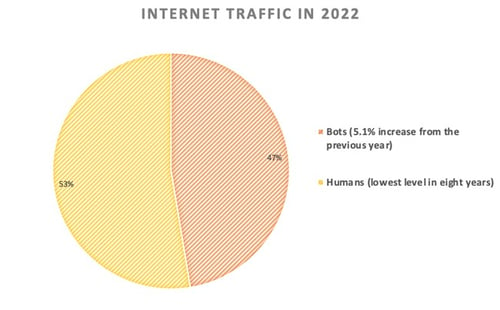
1. According to a recent report, bots accounted for a staggering 47.4% of total internet traffic in 2022, marking a significant 5.1% rise compared to the previous year. Interestingly, the study also revealed a notable decline in human traffic, reaching its lowest point in eight years at 52.6%. These findings shed light on the escalating prevalence of bots and the shifting dynamics of internet users.
 Internet Traffic in 2022
Internet Traffic in 2022
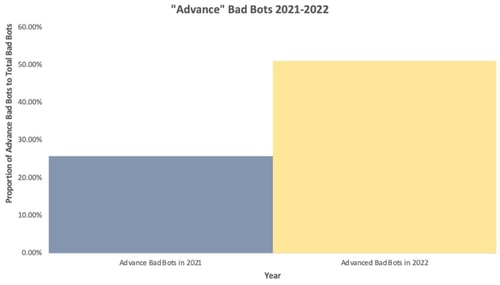
2. The year 2022 witnessed a noteworthy increase in the sophistication of bad bots, with "advanced" bad bots comprising 51.2% of the overall bad bot traffic. This represents a substantial surge compared to the 25.9% of advanced bad bots observed in 2021. These findings underscore the growing complexity and sophistication of malicious bot activities, emphasizing the need for robust cybersecurity measures to combat this evolving threat.
 Advanced Bad Bots 2021-2022
Advanced Bad Bots 2021-2022
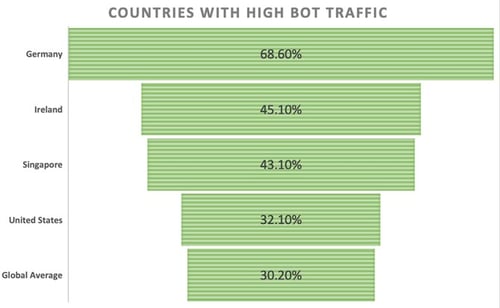
3. Out of the 13 countries examined in the report, seven exhibited levels of bad bot traffic, surpassing the global average of 30.2%. Taking the lead were Germany with 68.6%, Ireland with 45.1%, and Singapore with 43.1%. Notably, the United States also exceeded the global average, registering a bad bot traffic level of 32.1%.
Countries with High Bot Traffic
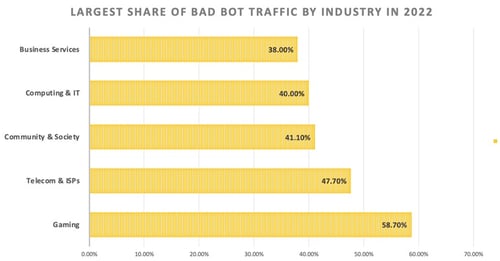
4. Gaming (58.7%) and telecommunications (47.7%) had the highest bad bot traffic on their websites and applications.
Largest Share of Bad Bot Traffic by Industry 2022
How bots are used for malicious purposes
Cybercriminals employ bots for various malicious activities, including:
1. Sending spam emails: Bots can be programmed to inundate inboxes with an overwhelming volume of spam emails. These unsolicited messages often contain malware, phishing links, or other deceptive content, intending to deceive unsuspecting recipients.
2. Spreading malware: Bots play a role in distributing malware, such as viruses, trojans, and ransomware. By exploiting vulnerabilities in computer systems, bots can swiftly infect devices, enabling cybercriminals to gain unauthorized access, pilfer sensitive data, or hold information hostage in exchange for ransom.
3. Launching denial-of-service attacks: Bots can orchestrate large-scale denial-of-service (DoS) attacks. In these instances, a network or server is flooded with excessive traffic, rendering it inaccessible to legitimate users. DoS attacks can disrupt online services, resulting in substantial financial losses and reputation damage.
The risks posed by bots to cybersecurity
The rise of bots as a cybersecurity threat entails several risks, including:
1. Data breaches: Bots can be exploited to breach security systems and pilfer valuable data. Personal information, such as credit card details, passwords, and social security numbers, can be harvested and employed for identity theft, fraud, or other malicious endeavors.
2. Systems compromise: With the ability to compromise computer systems, bots provide cybercriminals with unauthorized access to sensitive data. This can result in intellectual property theft, exposure of trade secrets, or compromise of financial information, leading to severe consequences for individuals and organizations.
3. Business disruption: Bot attacks can have detrimental effects on businesses. By overwhelming websites or servers, bots can cause service outages, resulting in lost revenue, decreased productivity, and decreased customer trust. Moreover, recovering from such attacks can be a time-consuming and costly process.
Bad bots at work
One cyber threat that targets user accounts on digital platforms is a credential stuffing attack. This tactic involves using automated bots or scripts with illegally obtained usernames and passwords to gain unauthorized entry into these user accounts. Typically, hackers exploit people’s inclination to re-use login details across several online entities like websites, social media platforms, and others across sectors/industries. During an infringement campaign using this method, script-enabled solutions systematically try various permutations, albeit rapidly, checking for matches that provide unauthorized account access. This approach's probability of success rests squarely on the assumption that abundant users regularly use identical login credentials for separate websites or internet-based applications.
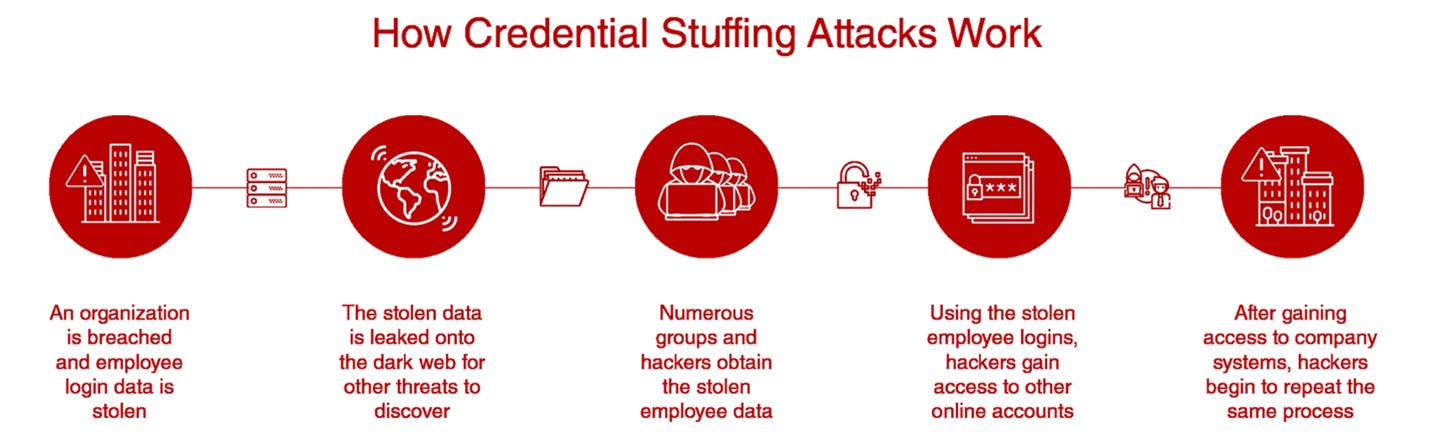 How Credential Stuffing Attacks Work
How Credential Stuffing Attacks Work
How to protect yourself from bot attacks
Safeguarding against bot attacks necessitates a proactive approach. Here are some essential steps you can take to protect yourself:
1. Use strong passwords: Enhance the security of your accounts by employing robust passwords. A strong password should consist of at least 12 characters, incorporating a combination of uppercase and lowercase letters, numbers, and symbols. Avoid using common phrases or quickly guessable information.
2. Keep your software up to date: Regularly update your software, including operating systems, applications, and security programs. Updates often encompass crucial security patches that address vulnerabilities and fortify defenses against evolving threats.
3. Exercise caution with links: Be vigilant when clicking links, particularly within emails or unfamiliar websites. Remain cautious of phishing attempts to deceive users into divulging sensitive information or downloading malware. Verify the legitimacy of sources before clicking on any links.
4. Utilize a firewall and antivirus software: Employ a reputable firewall and antivirus software to fortify your defenses against bots and other malicious threats. Ensure these tools are consistently updated to maximize their effectiveness in detecting and preventing attacks.
As the digital landscape evolves, bots become a significant cybersecurity threat. Their potential for engaging in malicious activities, such as spreading malware, launching DoS attacks, and compromising sensitive data, underscores the importance of vigilance.
By adhering to the recommendations outlined in this article, such as using strong passwords, keeping software up to date, exercising caution with links, and utilizing security tools, you can bolster your defenses against bot attacks. Stay informed, stay proactive, and safeguard your digital presence from this emerging cybersecurity menace.





