The accelerated adoption of cloud computing over the past decade has unlocked new levels of business agility, scalability, and cost efficiency. However, security has struggled to keep up with the rapid pace of cloud innovation. Misconfigurations, vulnerable services, advanced malware, and sheer scale have opened cracks in cloud security.
A new report from Qualys highlights critical security issues organizations face as they adopt cloud computing models. The 2023 Qualys TotalCloud Security Insights report provides data-backed insights into top vulnerabilities, ongoing threats, and remediation challenges in cloud environments.
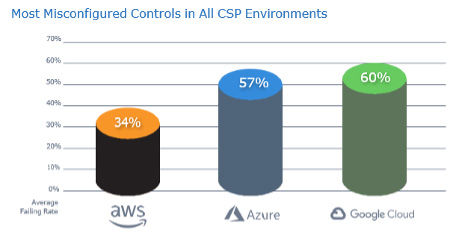
Cloud misconfigurations are rampant
Cloud configurations are growing in complexity, while many organizations lack the expertise to keep up, according to the report. The result is misconfigured controls that leave data exposed. The report mapping misconfigurations to MITRE ATT&CK tactics shows higher passing rates for early attack stages like reconnaissance, while later, more dangerous tactics have higher failure rates.
The research reveals high failure rates of 34-60% for security configuration benchmarks across Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP), as the graph below shows:
Zane Bond, Head of Product at Keeper Security, discussed these findings with SecureWorld News:
"Most successful attacks on cloud infrastructure these days stems from the same cause: misconfigurations.
Amazon Web Services (AWS), Google Cloud Platform (GCP) and Azure continuously upgrade and evolve their security recommendations. However, these components are not always implemented properly or monitored.
Administrators should always ensure they're using a secure vault and secrets management solution, and performing necessary patches and updates immediately. They should also check their cloud console's security controls to ensure they're following the latest recommendations. And as always, don't make risky clicks with suspicious emails."
External cloud assets face continuous threats
The report shows that approximately 4% of scanned cloud assets have public IP addresses, making them directly accessible from the internet. This expansive external attack surface enables attackers to easily identify and target vulnerable systems.
Shockingly, the data shows that about 51% of vulnerabilities on these internet-facing assets remain unpatched. The top external threats include both known critical vulnerabilities and Zero-Day exploits:
- Log4Shell and its secondary CVEs continue to grant access despite patches being available. 68% of external Log4Shell detections remain unpatched.
- Vulnerabilities in NGINX, Atlassian Confluence, VMware, MS Exchange, and other popular services also provide entry points.
- Sophisticated actors have proven adept at finding and weaponizing zero-day flaws before vendors can respond. For example, ProxyShell was exploited in the wild before public disclosure.
Utpal Bhatt, CMO of Tigera, validates this threat landscape, noting that:
"Threat actors are constantly targeting public clouds, looking for and finding vulnerabilities to exploit. Poorly secured cloud ingress ports, for example, help attackers gain unauthorized access and disrupt cloud-based workloads and data. Attackers also use other techniques, such as malicious software (malware), zero-day exploits, and account takeover, to breach public clouds."
Attackers often quickly develop exploit code and scripts for emerging external vulnerabilities in common services. Wormable threats then spread rapidly across the internet if unpatched systems are left exposed. Without proper cloud architecture and controls, these attacks can penetrate internally from compromised cloud assets.
Sophisticated malware penetrates cloud defenses
The Qualys report reveals that malware like cryptominers and advanced threats such as AndroxGh0st represent active exploitation within cloud environments. These stealthy malware strains evade traditional signature-based defenses.
AndroxGh0st in particular showcases sophisticated techniques to maintain persistence and lateral movement after penetrating clouds, which:
- Targets .env files to steal credentials and cloud access keys.
- Creates privileged IAM accounts and roles for itself.
- Abuses misconfigurations like weak IAM password policies to expand access.
- Uses compromised access to infect additional workloads and services.
Once inside the cloud perimeter, advanced malware leverages its persistent foothold to extract data, hijack resources, and damage systems while covering its tracks. Security researchers advise that AI-based malware detection is crucial for early discovery and rapid response.
Automation is a must for remediation
The report quantifies the vast difference in remediation speed enabled by automated cloud security tools. For non-Windows vulnerabilities, automated patching slashed average remediation time by two days compared to manual processes. It also boosted patch rates by 8%.
This data highlights that manual approaches simply cannot keep pace with the volume and velocity of change in cloud environments. Regular checks and immediate updates are essential for cloud security.
The report also reveals a critical influx of technical debt on the horizon. More than 35,000 applications will go end-of-support in the next 12 months. And more than 60 million outdated applications already reside in today's clouds.
Collaboration, new strategies needed for cloud security
As a shared responsibility, cloud security requires new collaborations and strategies aligned to the cloud model. The Qualys benchmarks reveal cracks on both sides. The report makes key recommendations for cloud-native tools like posture management, rapid patching, and AI-based malware detection. Working together, providers and users can close security gaps in the cloud.
The full report from Qualys is available here.
Follow SecureWorld News for more stories related to cybersecurity.





