Winning a prize is one of life's sweetest rewards—unless that prize is malware in disguise.
In a world hyper-focused on ransomware, a new and deeply devious trojan, named GriftHorse by Zimperium zLabs researchers, competes in dollars lost and far outweighs devices breached.
Researchers discovered this malicious software reached more than 10 million people through Android's Google Play Store and third-party app stores, resulting in millions of dollars stolen.
The cyber thieves floated by, undetected for months, due to the levels of sophistication involved in developing this nasty campaign against Android users.
GriftHorse trojan scope and apps infected
The scope of countries this malicious software landed in is astounding, spreading to app users in several dozen nations.
"The campaign has targeted millions of users from over 70 countries by serving selective malicious pages to users based on the geo-location of their IP address with the local language. This social engineering trick is exceptionally successful, considering users might feel more comfortable sharing information to a website in their local language," reads the report.
More than 200 apps were infected. This pie graph shows the top categories: 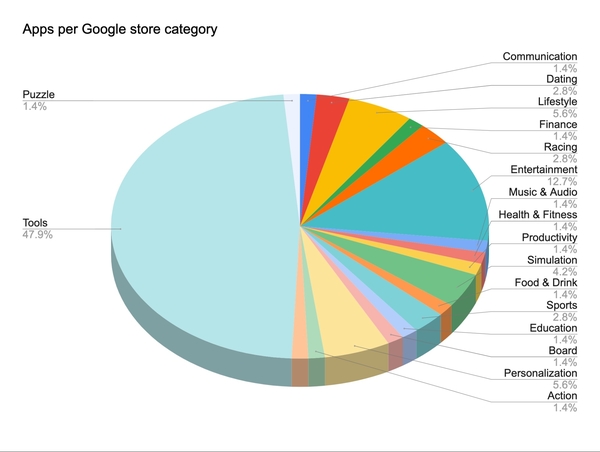
GriftHorse trojan social engineering technique
Once a user installed an infected app, a pop-up came onscreen alerting the user they had won a prize. This was the first step in the attack, which relied on both social engineering and persistence.
The research describes more about how this works, how attackers make money from the GriftHorse trojan, and why a successful attack often went unnoticed by victims:
"Upon infection, the victim is bombarded with alerts on the screen letting them know they had won a prize and needed to claim it immediately. These pop ups reappear no less than five times per hour until the application user successfully accepts the offer.
Upon accepting the invitation for the prize, the malware redirects the victim to a geo-specific webpage where they are asked to submit their phone numbers for verification. But in reality, they are submitting their phone number to a premium SMS service that would start charging their phone bill over €30 per month.
The victim does not immediately notice the impact of the theft, and the likelihood of it continuing for months before detection is high, with little to no recourse to get one's money back.”
On top of the sly methods to steal money, this attack went on for months:
"The campaign has been actively under development for several months, starting from November 2020, and the last updated time dates back to April 2021. This means one of their first victims, if they have not shut off the scam, has lost more than €200 at the time of writing. The cumulative loss of the victims adds up to a massive profit for the cybercriminal group."
While the technology developed to launch this attack was highly sophisticated, researchers highlighted the social engineering techniques used to encourage users to accept the malignant prize:
"Overall, GriftHorse Android Trojan takes advantage of small screens, local trust, and misinformation to trick users into downloading and installing these Android Trojans, as well frustration or curiosity when accepting the fake free prize spammed into their notification screens."
[RELATED: 5 Emotions Used in Social Engineering Attacks]
Perhaps worst of all, the malware is still active on third-party app stores.
Check out the full research report to see details about the GriftHorse trojan impacting Android devices.
[RESOURCE] Registration is open for SecureWorld Texas virtual conference. Gain access to top experts in cybersecurity and network with your peers, virtually.




