Security researchers at Checkmarx and Illustria recently discovered a campaign in which a threat actor(s) managed to post over 144,000 phishing packages to popular open source platforms, including NPM, PyPi, and NuGet.
The investigation between the two organizations revealed a new attack vector where the perpetrators spam open-source ecosystems with packages containing links to phishing campaigns.
The packages and related user accounts were likely created using automation, and they share similar project descriptions and auto-generated names. The threat actors also used referral IDs to retail websites to benefit from referral rewards.
The report discusses the use of a process Checkmarx and Illustria call "retro-hunting," where their "technology collects and indexes evidence related to packages from all open-source ecosystems, allowing us to query historical data for new insights and discover suspicious activities."
A few months ago, researchers discovered that clusters of packages had been posted in large quantities to the NuGet package manager.
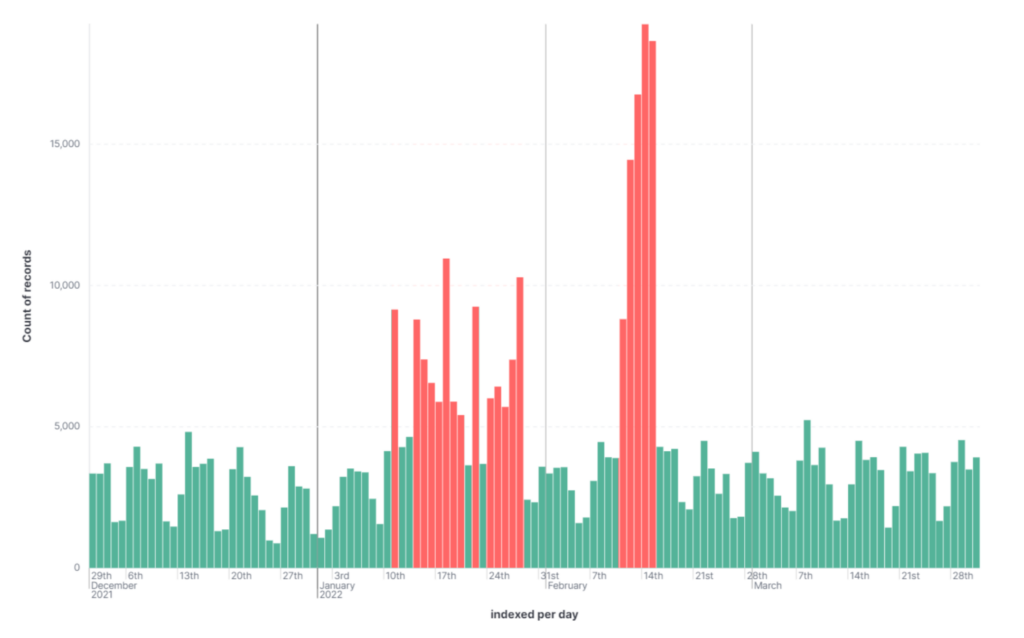
The report says:
"In this situation, it seems that automated processes were used to create over 135,000 packages in NuGet and related user accounts. The descriptions for these packages contained links to phishing campaigns. Our teams alerted the NuGet security team, and they replied that the packages were unlisted to protect users of the open-source ecosystem."
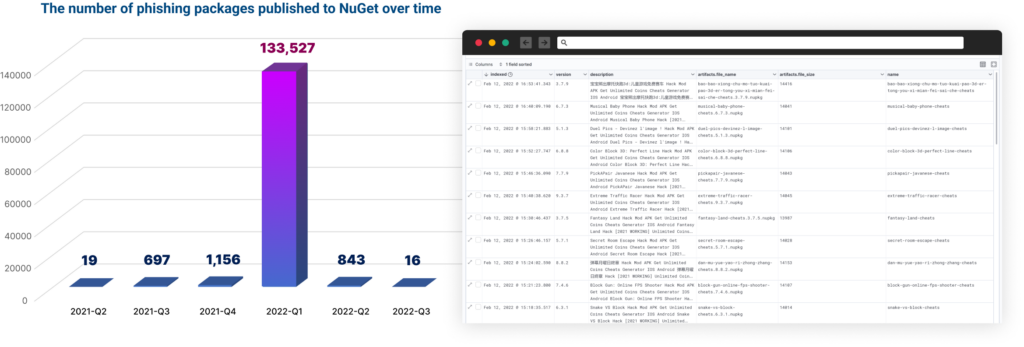
Further investigation revealed that similar activity had also taken place in NPM and PyPi. In total, 144,294 phishing-related packages were detected, all of which were created by the same threat actor. Of these, 136,258 were published on NuGet, 212 on NPM, and 7,824 on PyPi.
The report also notes the large scale of the NuGet package publication, and the patterns in the user accounts suggest that the process was automated.
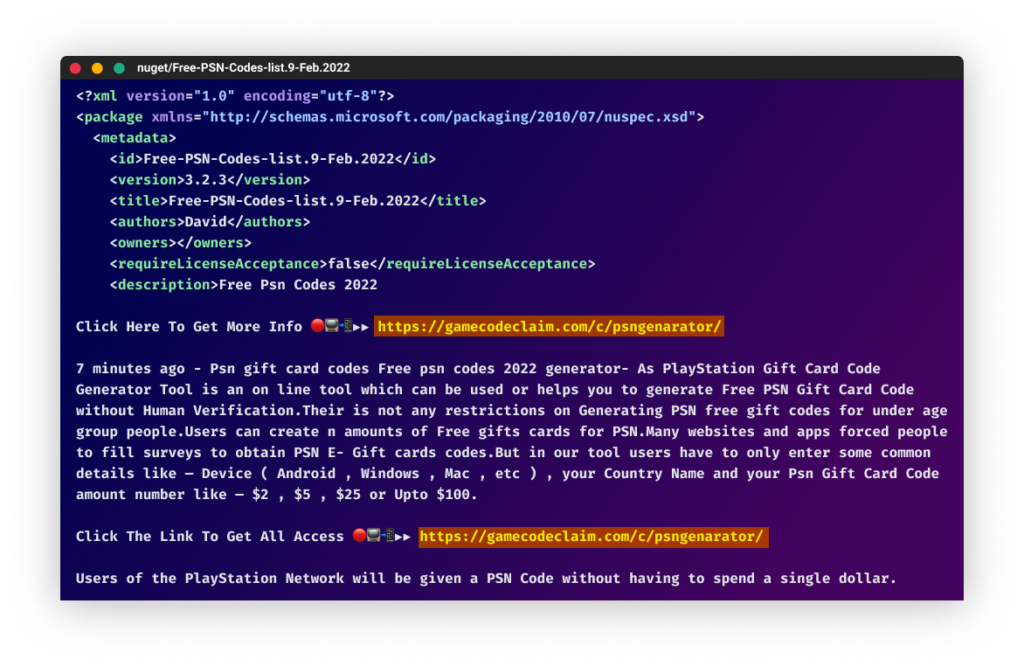
The majority of packages included names related to hacking, cheats, and free resources to promote their phishing campaign. Names such as "free-steam-codes-generator," "yalla-ludo-diamond-hack," "a3-still-alive-hack-diamonds," and "project-makeover-hack-gems" were designed to lure users into downloading the packages and clicking on the links to the phishing sites.
The messages in the campaign were crafted so that readers would click on links with promises of game cheats, free resources, and increased followers and likes on social media platforms like TikTok and Instagram.
The report concludes with this:
"These attackers invested in automation in order to poison the entire NuGet, PyPi, and NPM ecosystem with 144,294 packages. This allowed them to publish a large number of packages in a short period of time, making it difficult for the different security teams to identify and remove the packages quickly. Automating the process also allowed the attackers to create a large number of user accounts, making it difficult to trace the source of the attack. This shows the sophistication and determination of these attackers, who were willing to invest significant resources in order to carry out this campaign."
For more information, see the full report, How 140K Nuget, NPM, and PyPi Packages Were Used to Spread Phishing Links.
Follow SecureWorld News for more stories related to cybersecurity.





