In brief: The Windows event log and Event Viewer are supposed to help users diagnose security issues and other problems in PCs. However, Kaspersky researchers encountered one hacker who used the event log itself against their target.
Last week, Kaspersky published a detailed analysis of a complex attack that began last fall. It involved a combination of various techniques and pieces of software, but Kaspersky's security researchers highlighted the use of Windows event logs as something completely new.
At one stage of the hacking campaign, the attacker inserted shellcode into the target's Windows event logs. This method of storing malware is particularly stealthy because it leaves no files for antivirus to detect.
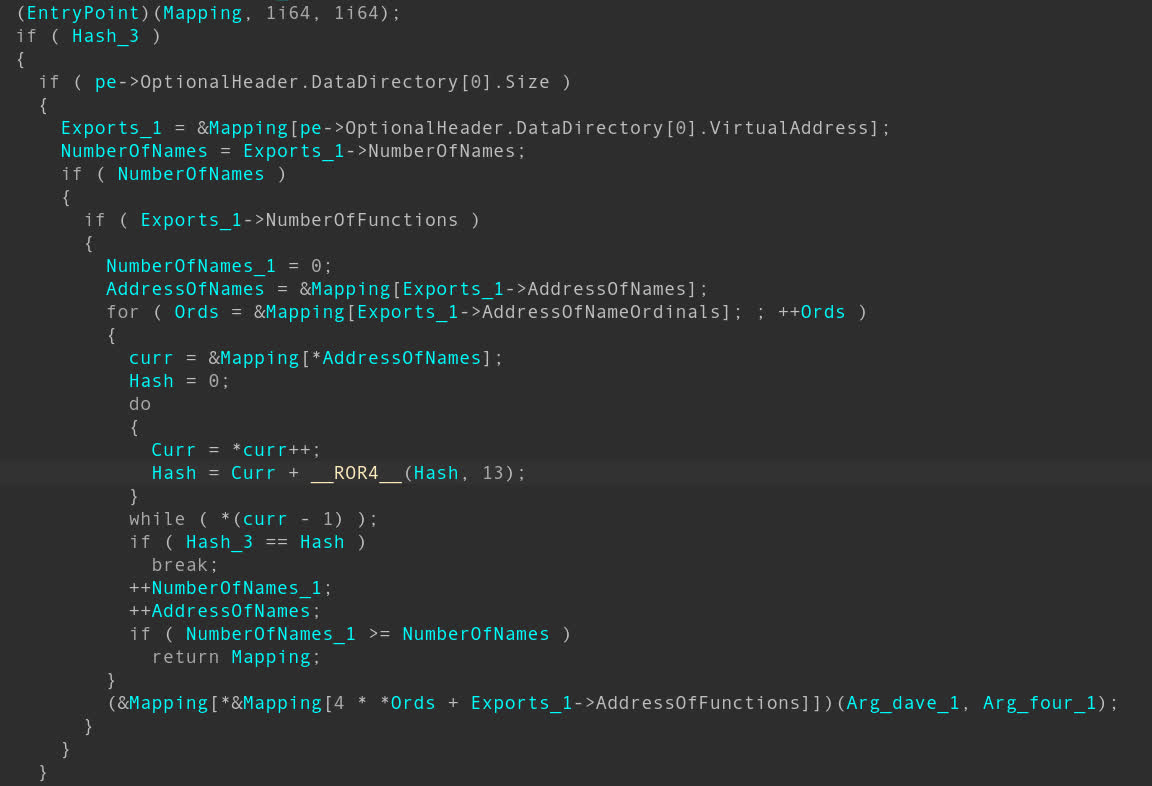
The campaign also involved a large suite of both commercial and home-brewed software. It involved DLL hijacking, a trojan, anti-detection wrappers, web domain mimicking, and more. The attacker even personally signed some of their custom software to make it look more legitimate.
The scale and uniqueness of the attack indicate it was tailored toward a specific target system. The first step involved social engineering, in which the attacker convinced the victim to download and run a .rar file from the legitimate file-sharing site file.io in September. If nothing else, this should be a reminder against clicking on links from strangers, much less downloading and running files from them.
Kaspersky couldn't link the attack to any known suspects, or determine its ultimate purpose. However, the researchers told BleepingComputer that similar attacks usually aim to grab valuable data from their targets.
