In a nutshell: Cybersecurity analysts recently discovered a strain of Android malware they dubbed "TangleBot." The malicious software is highly sophisticated and capable of hijacking most if not all of a phone's functions. Once infected, the phone becomes the ultimate spying/stalking device.
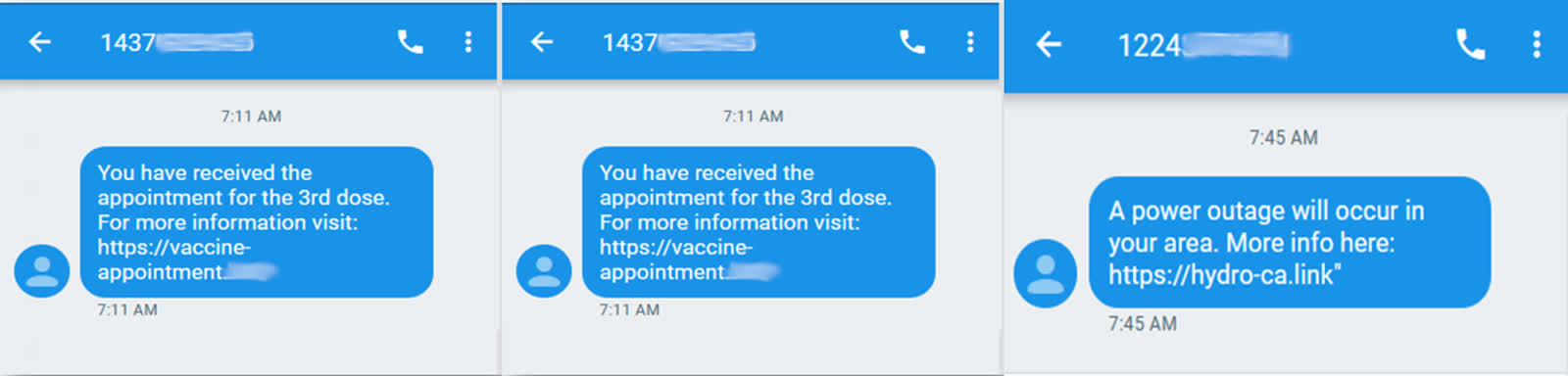
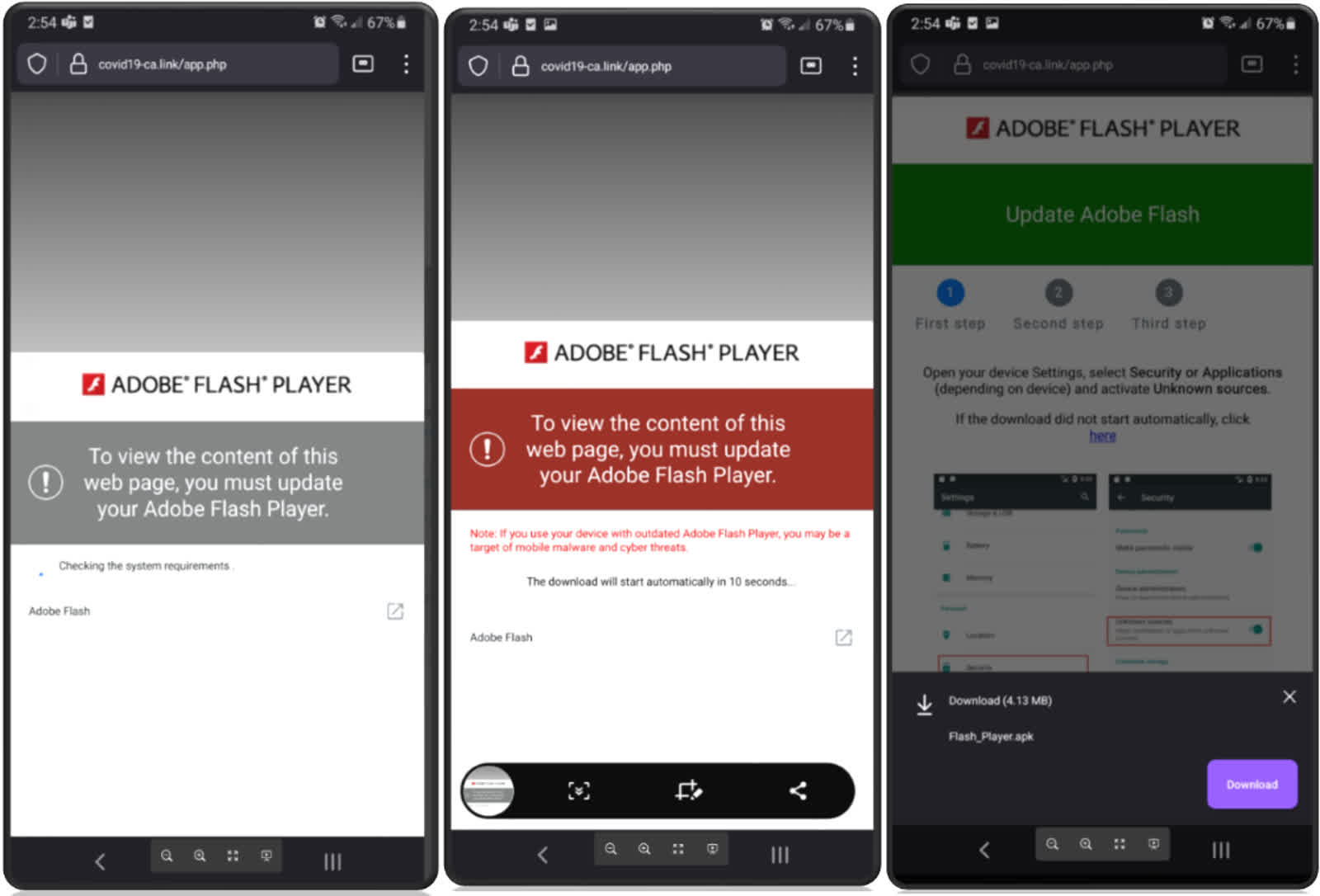
Proofpoint researchers note that TangleBot targets users by sending text messages to Android devices in the U.S. and Canada. The SMS messages are disguised as Covid-19 regulations and booster shots information, along with messaging related to potential power outages, encouraging victims to click a link to a site that shows an Adobe Flash update is required.
If the dialogue boxes are selected, the malicious site will install the malware onto the smartphone. The attackers are dependent on users being oblivious to Adobe stopping its support for Flash in December 2020 and the fact that it hasn't been supported on mobile devices since 2012.
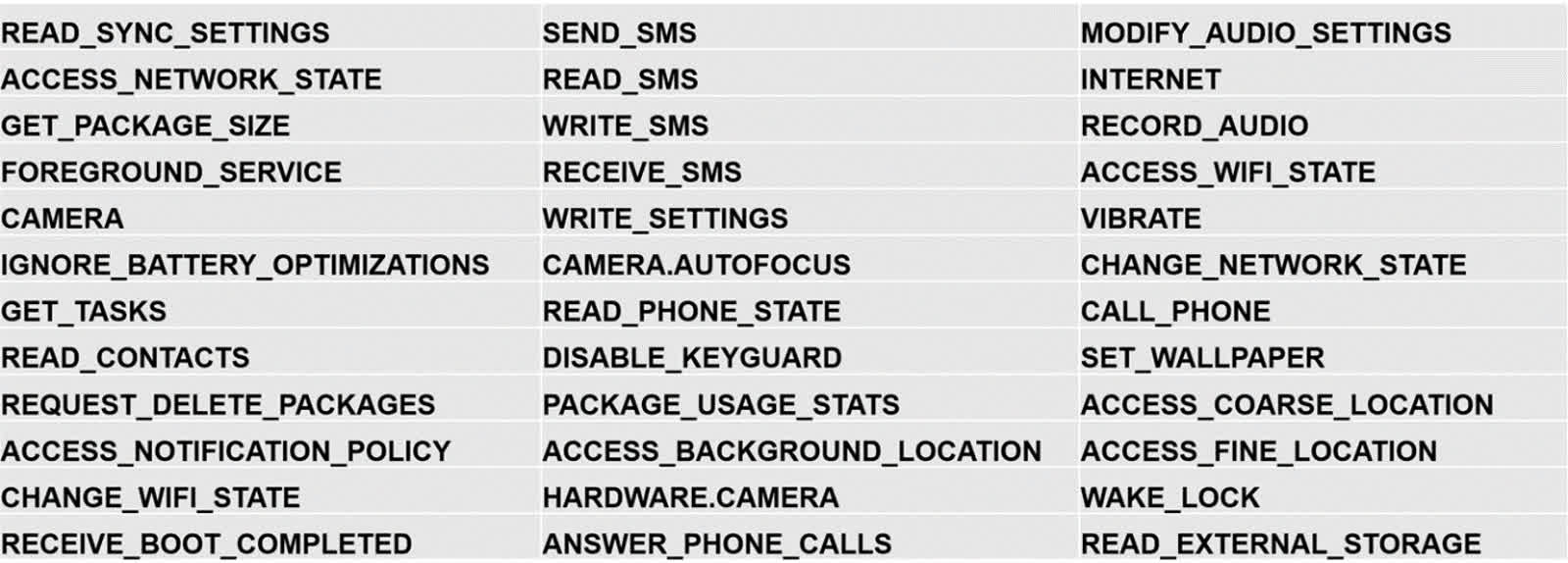
If successful in its deception, TangleBot can then completely infiltrate the entire phone. The malware can control audio and video from the microphone and camera, view websites visited, access the collection of typed passwords, extract data from SMS activity and any stored content on the device. TangleBot can also grant itself permission to modify device configuration settings and allow attackers to view GPS location data.
The functionality gained by the hackers essentially delivers total surveillance and data collection capabilities. TangleBot provides some key distinguishing features that make it especially threatening, including advanced behaviors, transmission abilities, and a string decryption routine for obfuscation.
In addition to its spyware and keylogging abilities, the malware can block and make calls, inevitably leading to the possibility of dialing premium services. Voice biometric identification capabilities, meanwhile, could be used to impersonate the victim.
The report noted that the level of complexity seen in TangleBot makes itself stand out among other forms of malware.
"Characteristics relating to keylogging functionality, overlay ability, and data exfiltration are routine behaviors in any malware arsenal, TangleBot, however, sets itself apart with advanced behaviors and transmission capabilities, while showcasing the latest evolutions in malware attempting to thwart biometric voice-authentication security systems. One final component of TangleBot not seen in the original Medusa is the advanced use of a string decryption routine helping to obfuscate and conceal the behavior of the malware."
The cutting-edge technology used to hide the purpose and functionality of the trojan software under many obfuscation layers is what led to the name TangleBot. Those methods include hidden .dex files, modular and functional design characteristics, minified code, and large amounts of unused code.
Android malware and trojans are becoming increasingly common for Google's operating system, and it's not just through text messages where a smartphone can be exposed. The GriftHorse malware was successfully embedded into apps officially approved for Google Play and other third-party app stores, allowing it to infect more than 10 million devices and steal tens of millions of dollars.
It's a worrying state of affairs for Android, echoed by the researcher's closing statement in the report.
"If the Android ecosystem has shown us anything this summer, it is that the Android landscape is rife with clever social engineering, outright fraud, and malicious software all designed to deceive and steal mobile users' money and other sensitive information," said the team. "These schemes can appear quite convincing and may play on fears or emotions that cause users to let down their guard."
Those remarks are clearly outlined by security firm Eset's recent analysis showing how Android malware is growing across multiple threat areas.