Apple Passkeys: No Panacea for User Device Security
IT Toolbox
DECEMBER 14, 2022
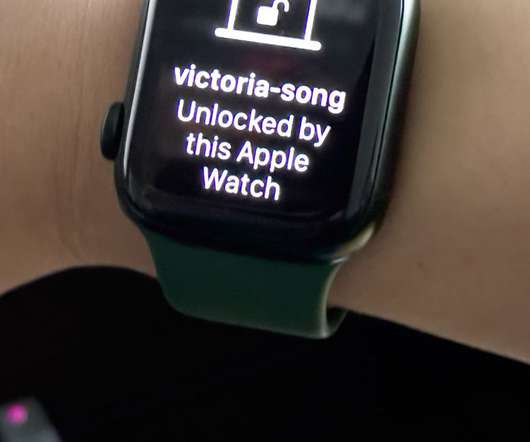
Digital services require complex passwords and dual authentication to improve user experience and device security. The post Apple Passkeys: No Panacea for User Device Security appeared first on.



















































Let's personalize your content