6 Best Authenticator Apps for 2024
Tech Republic Security
MARCH 26, 2024
Authenticator apps provide an extra layer of security. Learn about the best authenticator apps to secure your online accounts and protect your privacy.
 Authentication Related Topics
Authentication Related Topics 
Tech Republic Security
MARCH 26, 2024
Authenticator apps provide an extra layer of security. Learn about the best authenticator apps to secure your online accounts and protect your privacy.

IT Toolbox
DECEMBER 4, 2023
Authentication allows the verification of user identity, ensuring only authorized access to systems, services, and resources. The post What Is Authentication? Meaning, Types, and Tools appeared first on Spiceworks.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Tech Republic Security
MARCH 5, 2024
Learn about passwordless authentication, and explore the different types, benefits and limitations to help you decide which solution to choose.

Tech Republic Security
APRIL 2, 2024
Discover the top passwordless authentication solutions that can enhance security and user experience. Find the best solution for your business needs.

Advertiser: ZoomInfo
Marketing and sales teams are feeling pressured to deliver authentic messaging to buyers at every point of their customer journey. 47% of marketers said they have a database management strategy in place, but there is room for significant improvement.
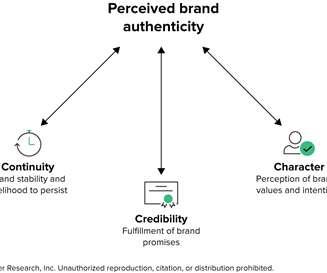
Forrester IT
APRIL 5, 2022
As the age of misinformation and slew of dubious corporate claims threaten consumers’ trust in brands, consumers are desperate for authenticity. While conventional wisdom suggests that authenticity means “being yourself,” that quickly breaks down when CMOs translate the sentiment into action.

Tech Republic Security
MARCH 20, 2024
Explore top multi-factor authentication solutions for enhanced security and user authentication. Learn about the benefits and features of leading MFA providers.

Advertisement
User authentication and advanced security factors. The following checklist is built to help you evaluate the scope of services offered by various encryption solutions on the market and covers questions on the following topics: Encryption. Key management system. Enterprise features. Flexibility and scalability.

Advertiser: ZoomInfo
Conversations have always been at the heart of our most authentic relationships. Whether it’s a business deal or a personal connection, they are a driving force to solidify a foundation of trust. Enter conversational marketing — the new paradigm to tackling your business deals and converting prospects in minutes.

Advertisement
Think your customers will pay more for data visualizations in your application? Five years ago they may have. But today, dashboards and visualizations have become table stakes. Discover which features will differentiate your application and maximize the ROI of your embedded analytics. Brought to you by Logi Analytics.
Let's personalize your content