Caution And Lack Of Understanding Steer UK Consumer Attitudes Towards Generative AI
Forrester IT
APRIL 25, 2024
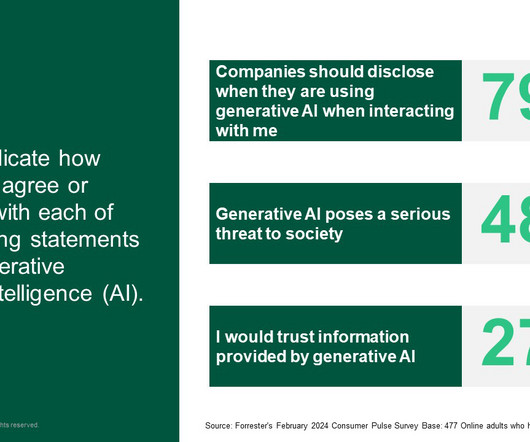
As the EU grinds the gears into action on the AI Act, the UK and US recently announced a “landmark agreement” on AI testing that broadly glosses over the lack of any firm governmental action in either country (other than executive orders and some Bletchley Park posturing last year). But do UK consumers care?











































Let's personalize your content