Using WireGuard on macOS
Scott Lowe
APRIL 1, 2021
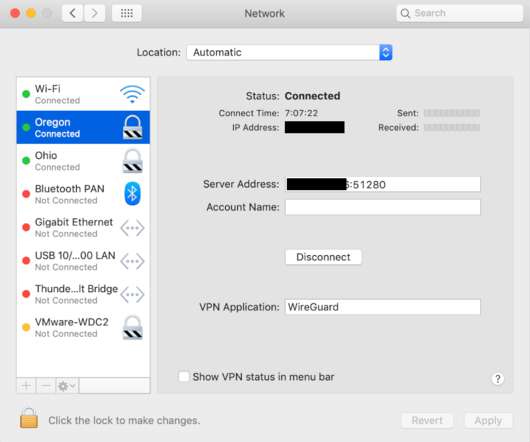
It’s an interesting sort of mismatch to have such a well-designed graphical application, but not provide any guidance or structure to the user on how to configure the interface/tunnel. Ultimately, you’d need the configuration to look something like this: [Interface] PrivateKey =. Peer] PublicKey =. AllowedIPs =. Endpoint =.



















Let's personalize your content