Imaging using MDT with Autopilot
Mick's IT Blog
SEPTEMBER 6, 2022
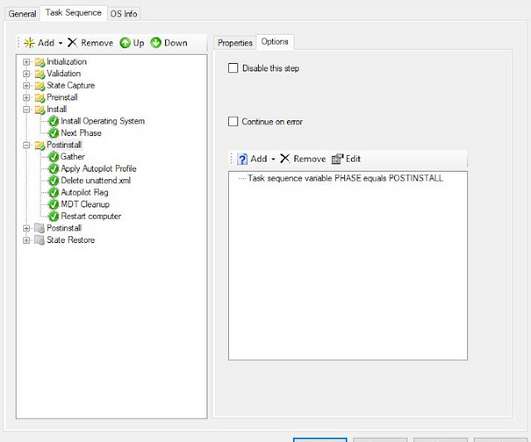
Finally, the Restart task reboots the system at which point it will come up to the Autopilot user signon page. Here is the program page. This is a flag to run the Intune package that will delete all MDT associated files and registry keys to terminate the MDT build. The next task will delete most of the MDT files on the system.

























Let's personalize your content