The Toll of Ransomware is Growing
CTOvision
MARCH 22, 2017
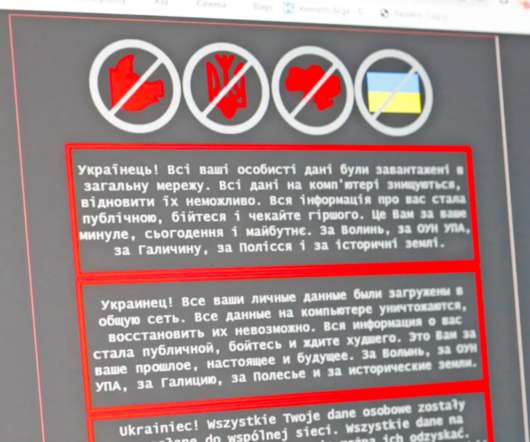
Ransomware is different than other malware and viruses because it is nearly impossible to break on your own. The best way to protect against ransomware is to have a strong series of backup solutions. A number of companies offer round-the-cloud backup support and can instantly spring into action in case ransomware is detected.






































Let's personalize your content