Device Configuration Profile Settings View-Intune Troubleshooting
Anoop
NOVEMBER 6, 2018
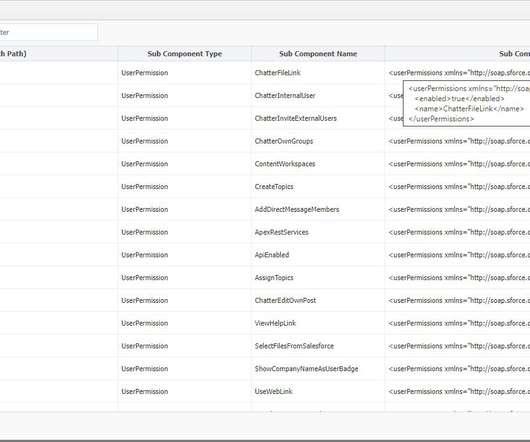
Have you notices an option in Intune troubleshooting blade to get into each set of device configuration profile? Intune Device Configuration profile settings view helped me to troubleshoot restriction policy deployments. All these two steps […].

















































Let's personalize your content