Using WireGuard on macOS
Scott Lowe
APRIL 1, 2021
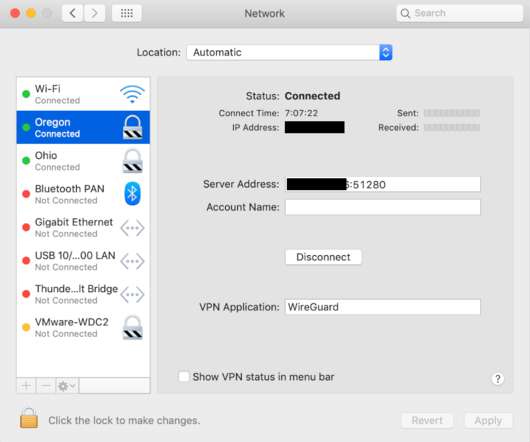
However, WireGuard is not limited to Linux, and I recently configured one of my macOS systems to take advantage of this WireGuard infrastructure for access to the private subnets in my AWS VPC. Hopefully this link will take you directly there if you’re on a macOS-based system.). Peer] PublicKey =. AllowedIPs =. Endpoint =.


















Let's personalize your content