Setting up Wireguard for AWS VPC Access
Scott Lowe
FEBRUARY 22, 2021
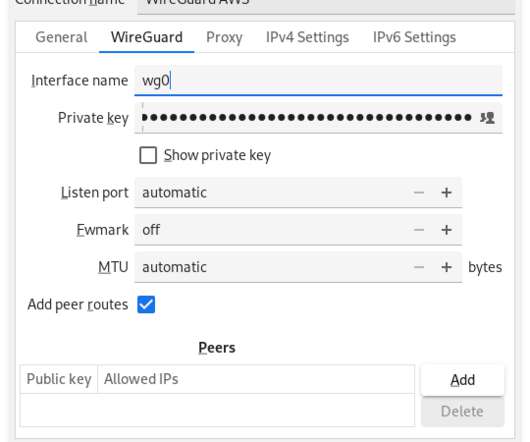
At a high level, the process looks like this: Installing any necessary packages/software. The first thing to do, naturally, is install the necessary software. Installing Packages/Software. This page on the Wireguard site has full instructions for a variety of operating systems. Activating the VPN.














Let's personalize your content