DTWS: New research finds the path to telco growth is through security, IoT, cloud
TM Forum
SEPTEMBER 23, 2021
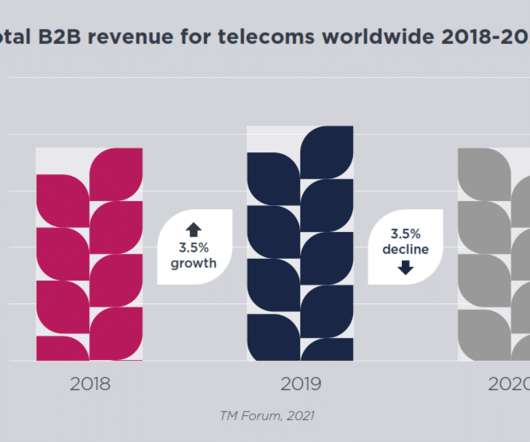
New research from TM Forum’s Research & Media team shows that the most promising B2B services include security, IoT and cloud, with double-digit percentage growth possible for each into 2024. On the one hand we’re saying that growth is all in IoT, security and cloud, but is that services? external_url. external_url.










































Let's personalize your content