MIT's minuscule terahertz RFID tag foils counterfeiters with metallic glue
TechSpot
FEBRUARY 20, 2024
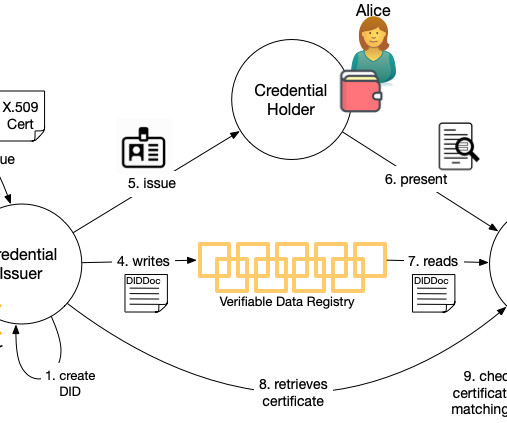
In 2020, MIT improved radiofrequency identification technology by designing a cryptographic tag several times smaller and cheaper to make than traditional RFID tags. It improved the security of standard RFID authentication by using terahertz radio waves. Read Entire Article












































Let's personalize your content