Zero Trust with Zero Data
Phil Windley
FEBRUARY 14, 2024
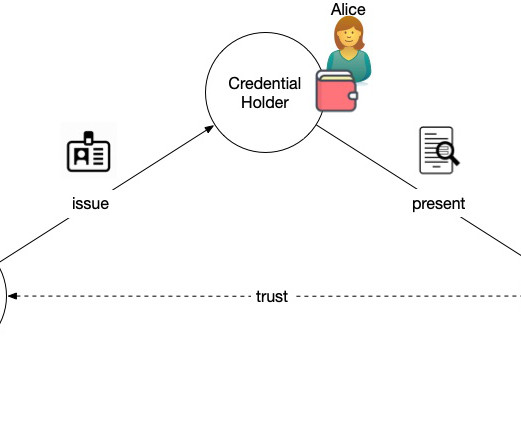
Summary: The physical world is full of zero trust examples, but they gather attributes for the access control decisions in a very different way than we're used to online. If we assume breach, then the only strategy that can protect the corporate network, infrastructure, applications, and people is to authorize every access.






























Let's personalize your content