Operationalizing Digital Relationships
Phil Windley
NOVEMBER 9, 2020
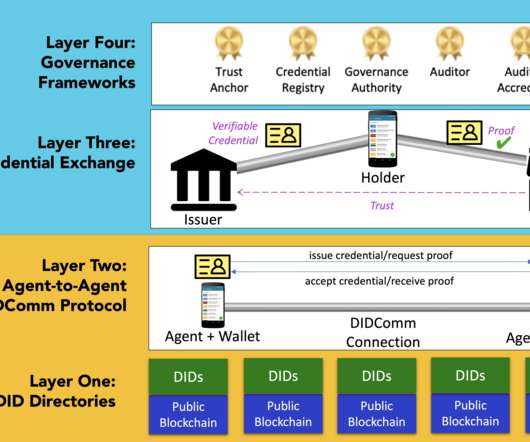
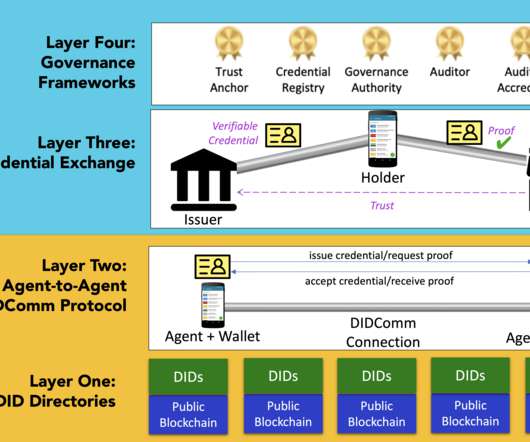
The credential they issue is founded on the credential definition and public DID (an algorithmic identifier) that Attester Org wrote to the ledger. As a credential issuer, Attester Org has an algorithmic identifier in the form of a public DID that has been recorded on the ledger. When Alice later needs to prove something (e.g.
























Let's personalize your content