Prioritizing AI? Don’t shortchange IT fundamentals
CIO Business Intelligence
FEBRUARY 14, 2024
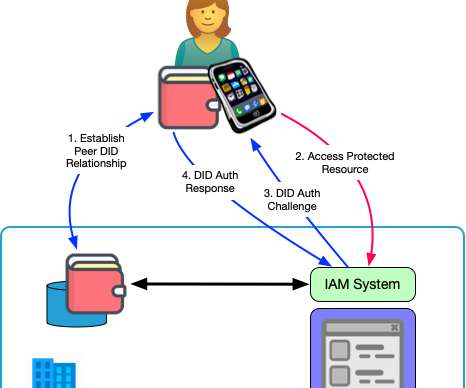
Fundamentals like security, cost control, identity management, container sprawl, data management, and hardware refreshes remain key strategic areas for CIOs to deal with. Containers and certificates Privilege management depends on identity management, another area that demands continued attention. And that’s going to constantly change.”






















Let's personalize your content