Using X.509 Certs for DID Provenance
Phil Windley
APRIL 25, 2024
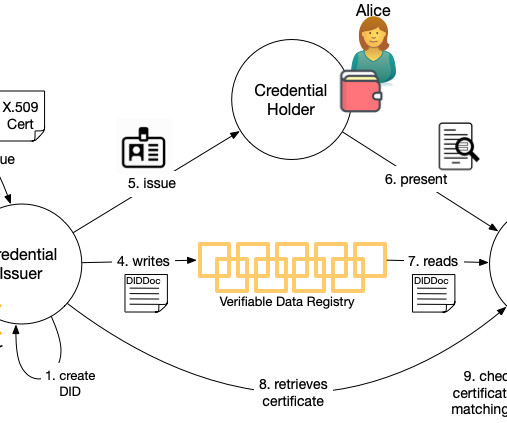
509 certificate authorities who already perform identity proofing for businesses provides a rich resource that can be leveraged to boot the verifiable data ecosystem. The issuer creates a credential definition in the usual way that includes their DID and writes it to whatever Verifiable Data Registry their DID method dictates.
















































Let's personalize your content