Is there a natural contradiction within AI-driven code in cloud-native security?
CIO Business Intelligence
JUNE 3, 2024
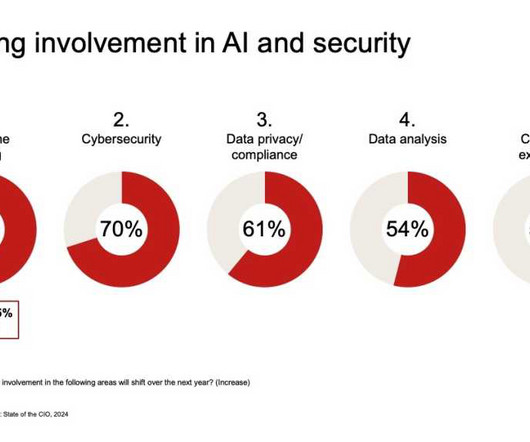
AI-generated code promises to reshape cloud-native application development practices, offering unparalleled efficiency gains and fostering innovation at unprecedented levels. This dichotomy underscores the need for a nuanced understanding between AI-developed code and security within the cloud-native ecosystem.













































Let's personalize your content