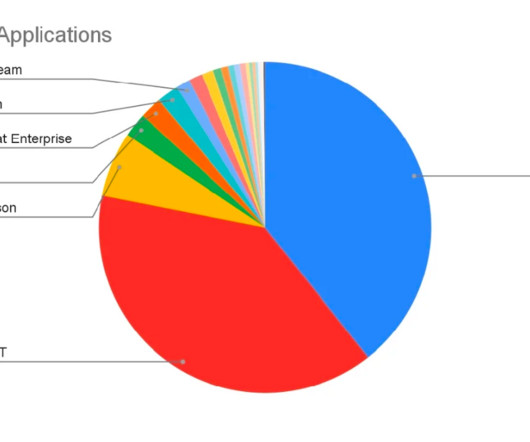
Secure Windows Devices with Intune Application Control Policy Managed Installers
Anoop
JULY 4, 2023
Read More The post Secure Windows Devices with Intune Application Control Policy Managed Installers appeared first on HTMD Community Blog #1 Modern Device Management Guides by Jitesh Kumar. Hello - Here is the new HTMD Blog Article for you. Enjoy reading it.



















































Let's personalize your content