Current Malpractice Handicaps Social Selling’s Potential
Forrester IT
AUGUST 5, 2019
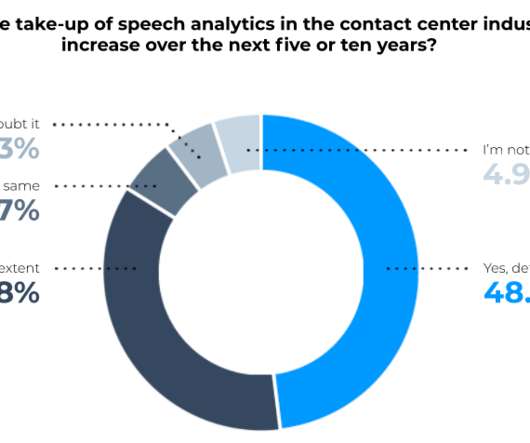
We first published research on social selling in 2016, and B2B sellers continue to flock to various networks to interact with their customers and prospects. Social provides the opportunity for authentic connections, mutually beneficial professional relationships, and positive business outcomes for both buyers and sellers.



















































Let's personalize your content