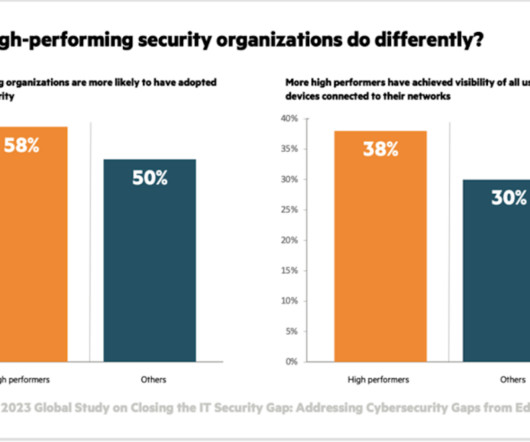
What’s next for network operations
CIO Business Intelligence
MARCH 20, 2023
By Serge Lucio, Vice President and General Manager, Agile Operations Division This is a continuation of Broadcom’s blog series: 2023 Tech Trends That Transform IT. Stay tuned for future blogs that dive into the technology behind these trends from more of Broadcom’s industry-leading experts.















































Let's personalize your content