Break The Cycle Of Security And Technology Intergenerational Trauma
Forrester IT
SEPTEMBER 12, 2023
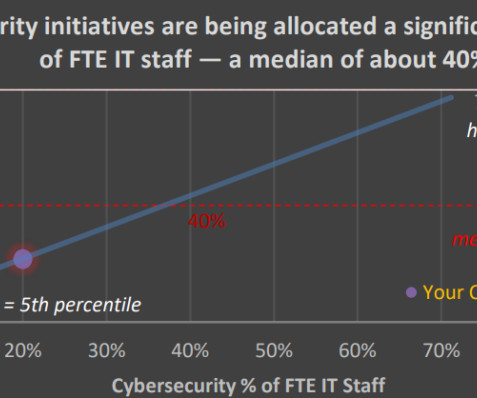
I’m thrilled to announce our latest research into a problem as old as time (or, at least, my time — 25 years! — in security): the silos between technology and security teams. How big is the problem? Officially, it’s not — according to numerous global technology decision-makers who we survey, cybersecurity is a top priority.









































Let's personalize your content