Why Can’t My Sellers Adapt More Quickly?
Forrester IT
MARCH 6, 2024
How recently did your company leadership issue a directive implying that the sales team must change their behavior? Not long ago, if yours is like most revenue organizations.

Forrester IT
MARCH 6, 2024
How recently did your company leadership issue a directive implying that the sales team must change their behavior? Not long ago, if yours is like most revenue organizations.

IT Toolbox
MARCH 6, 2024
A vast volume of 2FA security codes were leaked from an unsecured database, exposing Google, Facebook, and WhatsApp accounts. Find out how this leak occurred and about its implications for users. The post Massive Database of Google, Facebook, and WhatsApp 2FA Codes Leaked appeared first on Spiceworks.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Forrester IT
MARCH 6, 2024
We recently published the Top Recommendations For Your Security Program, 2024 report for CISOs and other senior cybersecurity and technology leaders. The theme for our annual recommendations report this year centers around the importance of anticipating and leading change. In 2024, our recommendations fall into three major themes for security leaders: Changing tech.

IT Toolbox
MARCH 6, 2024
Discover AI’s role in cybersecurity: threat detection, post-incident analysis, and cost-effective data protection. The post What Organizations Need To Know About AI-driven Cybersecurity appeared first on Spiceworks.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.
Forrester IT
MARCH 6, 2024
Read part one of the GenAI Impact On Commerce Tech blog series from Forrester Research principal analyst Emily Pfeiffer and senior researcher Nicole Murgia.

IT Toolbox
MARCH 6, 2024
This Women’s Day, learn about strategies to create a supportive workplace for women in STEM with immersive technology. The post How Technology Can Reduce Burnout Among Women in STEM appeared first on Spiceworks.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

IT Toolbox
MARCH 6, 2024
Explore how AI innovations can address longstanding barriers and create opportunities for women in the workplace. The post Women for Leadership: AI’s Role in Advancing Gender Equality appeared first on Spiceworks.

Information Week
MARCH 6, 2024
In today's tense geopolitical world, the initial thought about the cause of major outages is that they are due to cyberattacks. Fortunately, yesterday’s outages of Meta services appear to be the result of technical problems.

IT Toolbox
MARCH 6, 2024
Learn how to balance productivity, culture, and network performance during the NCAA tournament. The post How To Manage March Madness in the Work Environment? appeared first on Spiceworks.

Information Week
MARCH 6, 2024
Calling the action the “first of its kind,” the US said the spyware company’s software was used against government officials and other US interests.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

IT Toolbox
MARCH 6, 2024
Learn how CSaaS addresses complex cybersecurity challenges, providing expert support and cutting-edge technology. The post Understanding Cybersecurity as a Service: Offering Protection on Demand appeared first on Spiceworks.

Information Week
MARCH 6, 2024
AI isn't going to put human network managers out of work. It will, however, help managers become more insightful and efficient.

IT Toolbox
MARCH 6, 2024
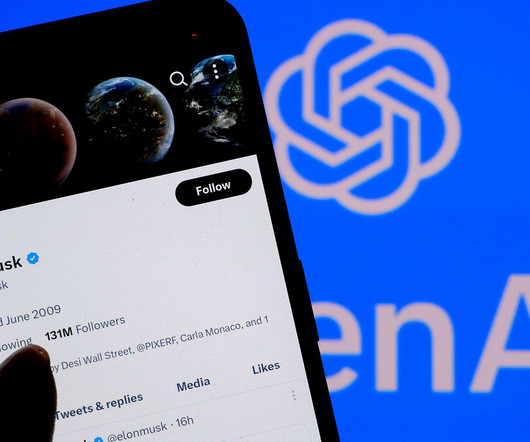
The drama follows OpenAI into March 2024 as Elon Musk sues CEO Sam Altman and the company for breaching the founding agreement. OpenAI and Altman hit back at billionaire technocrat Elon Musk for suing them for what the latter believes is a fight for the company’s approach to AI development. Here’s the latest. The post Elon Musk Kicks Off Battle of the Technocrats, Sam Altman Responds appeared first on Spiceworks.
Information Week
MARCH 6, 2024
The ChatGPT parent company says Elon Musk was supportive of for-profit restructuring and wanted to be CEO and have board control.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

IT Toolbox
MARCH 6, 2024
Over 200,000 compromised ChatGPT credentials have been found on dark web marketplaces between 2022 and 2023. Learn about the threat’s details and the cybersecurity incident’s implications. The post Stolen ChatGPT Credentials Found for Sale on Dark Web appeared first on Spiceworks.

Information Week
MARCH 6, 2024
In today's digital age, layoffs can go viral, impacting brand and culture. Learn to navigate terminations to foster resilience and loyalty.

IT Toolbox
MARCH 6, 2024
A real-time operating system (RTOS) is a specialized operating system designed to handle time-critical tasks. Learn more about RTOS, its types, uses, and a few examples from this article. The post What Is a Real-Time Operating System (RTOS)? Meaning, Working, Types, Uses, and Examples appeared first on Spiceworks.

TechSpot
MARCH 6, 2024
Navalny's funeral on March 1 was filled with supporters defying Russia's strict laws against pro-Ukrainian speech. One woman was captured on video saying "Glory to the heroes," the traditional response to the salute "Glory to Ukraine." She was charged with "displaying a banned symbol" and handed a small fine, but.

Advertisement
You’ve read the PMBOK® Guide several times, taken the certification exam for project managers, passed, and you are now a PMP®. So why do you keep making rookie mistakes? This whitepaper shows 20 of the most common mistakes that young or inexperienced project managers make, issues that can cost significant time and money. It's a good starting point for understanding how and why many PMs get themsleves into trouble, and provides guidance on the types of issues that PMs need to understand.

IT Toolbox
MARCH 6, 2024
Learn the essential steps and strategies for safeguarding consumer privacy in the Adtech landscape. The post Privacy Questions Brands and Advertisers Need to Ask Adtech Partners appeared first on Spiceworks.

Anoop
MARCH 6, 2024
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link] The post 2 Methods to View Reserved Storage Size in Windows 11 appeared first on HTMD Community Blog #1 Modern Device Management Guides by Krishna R.

GeekWire
MARCH 6, 2024
Marcus Lemonis. (Beyond Photo) Zulily’s back. The embattled online retailer, which laid off hundreds of employees last year as part of a surprising shutdown, appears to be relaunching in a remarkable new chapter. The company’s social media accounts sent a message Wednesday evening: “The only purple that saves you money. Coming soon.” Marcus Lemonis , the TV star of CNBC reality show The Profit , posted the same message on Wednesday from his own account.

CIO Business Intelligence
MARCH 6, 2024
IT industry researchers believe the biggest impact of gen AI this year will be in customer experience (CX), with organizations using vast amounts of data to communicate with consumers and resolve problems faster. Technology specialist Salesforce reports that more than two-thirds of service professionals believe gen AI will help them serve their customers better, while Forrester expects it to give CX teams a huge boost through 2024.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

GeekWire
MARCH 6, 2024
A high school student using technology for homework assignments. (GeekWire Photo / Lisa Stiffler) Despite technology seeping into practically every corner of our lives, computer-related education in Washington is woefully limited. Last year, 8.4% of the Washington’s high school students attending either public or state-tribal schools took a computer science class, according to state data.

Tech Republic Security
MARCH 6, 2024
Having a hard time getting started with Norton VPN? Learn how to use Norton Secure VPN with our in-depth tutorial.

CIO Business Intelligence
MARCH 6, 2024
Operational technology (OT) organizations face increasing challenges when it comes to cybersecurity. Manufacturing in particular has become a bigger target for bad actors; in fact, it was one of the sectors most impacted by extortion attacks, according to Palo Alto Networks’ 2023 Unit 42 Extortion and Ransomware Report. As Industry 4.0 continues to roll out, the internet of things (IoT) is expanding, and manufacturing organizations are using the latest technologies to scale.

TechSpot
MARCH 6, 2024
Apple finished second with 78 million smartphone shipments, up eight percent compared to the same period a year earlier. Qualcomm placed third with 69 million chip shipments, an increase of just one percent versus Q4 2022.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Anoop
MARCH 6, 2024
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link] The post Microsoft Ends Support for Running Android Apps on Windows 11 appeared first on HTMD Community Blog #1 Modern Device Management Guides by Krishna R.
TechSpot
MARCH 6, 2024
The JEDEC Solid State Technology Association recently announced the final version of the new GDDR7 memory standard. Open specifications for the JESD239 Graphics Double Data Rate (GDDR7) SGRAM tech are available for download from the JEDEC website, and they're poised to provide all the memory bandwidth needed by future high-performance.

Anoop
MARCH 6, 2024
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link] The post Start Menu Stop Working in Windows 11 Insider Preview Build appeared first on HTMD Community Blog #1 Modern Device Management Guides by Vidya M A.

Tech Republic Big Data
MARCH 6, 2024
Data management has become critical to drawing value from generative AI, according to research from Informatica. Senior VP for the Asia-Pacific region Richard Scott argues cloud architecture is key.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.
Let's personalize your content