3 things that make a CIO-CFO dream team
CIO Business Intelligence
JUNE 30, 2023
“There are plenty of good CIOs and plenty of good CFOs,” says Jim McGittigan, Research VP in the CIO Research group of Gartner. “Part of what makes them good is they understand one another. When they work well together, it has a huge impact on the effectiveness of the organization.” CIOs and CFOs who have this chemistry know that the relative success of the relationship runs along three dimensions: The reporting structure : “Where the CIO reports should fit the nature of the business,” says McGi


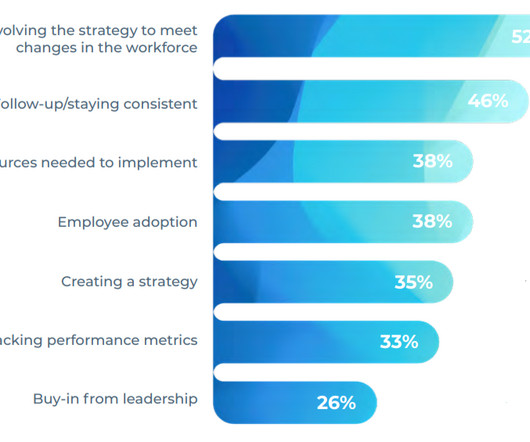






































Let's personalize your content