Have You Developed Your Journey-Centric Transformation Roadmap?
Forrester IT
NOVEMBER 23, 2023
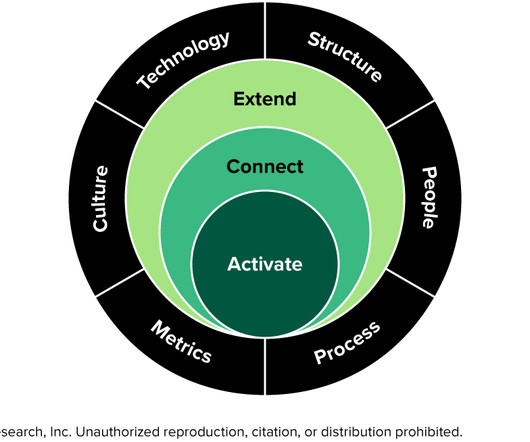
Use Forrester’s Assessment To Develop Your Journey-Centric Transformation Roadmap Journey centricity requires a change in operating model, moving six operational levers in concert, through three phases of transformation: activate, connect, and extend. It requires a clear plan to guide progress across levers, journey teams, and geographies.









































Let's personalize your content