IT Leaders as Advocates for Continual Change
Information Week
APRIL 4, 2023
While IT leaders have their finger on the pulse of tech advances, it’s crucial to work closely with business leaders ensuring strategy is aligned with business outcomes.

Information Week
APRIL 4, 2023
While IT leaders have their finger on the pulse of tech advances, it’s crucial to work closely with business leaders ensuring strategy is aligned with business outcomes.
IT Toolbox
APRIL 5, 2023
Watch out for these three trends in enterprise architecture. The post Three Trends in Enterprise Architecture to Optimize IT Operations appeared first on Spiceworks.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Information Week
APRIL 5, 2023
Quantifying the value of cybersecurity can be challenging, but making a business case helps IT leaders push for critical investments when it’s time to make budget decisions.

Information Week
APRIL 5, 2023
How can enterprises prepare for the next round of data privacy activity? This curated guide offers information and articles that will help IT leaders stay up to date.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Information Week
APRIL 5, 2023
Wazuh aims to provide a high-quality cybersecurity solution with excellent support and continuous innovation to all businesses, regardless of their size or budget.

IT Toolbox
APRIL 4, 2023
Is cloud repatriation just hype? Find out. The post Is Cloud Repatriation a Big Lie Server Vendors Are Shilling? appeared first on Spiceworks.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

IT Toolbox
APRIL 3, 2023
Check out what the year ahead looks like for HR practitioners. The post The Top Four Workplace Trends that will Impact Organizations This Year appeared first on Spiceworks.

Association of Information Technology Professional
APRIL 7, 2023
With all the hacking, phishing scams and unethical cyber behavior these days, we’re all on Team Cybersecurity. But did you know that there are two sides of that team? Read more to see if your skills match up to a red or blue team cybersecurity career.
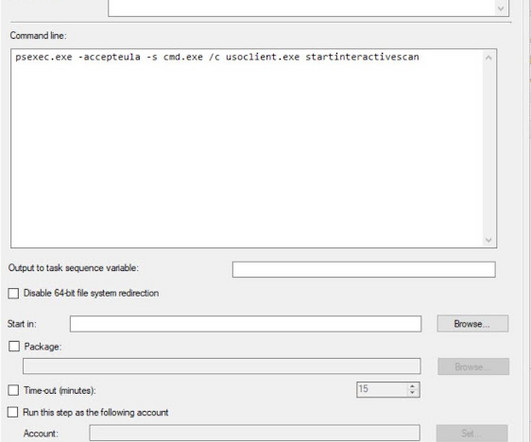
Mick's IT Blog
APRIL 7, 2023
I've been meaning to share this blog post for some time now, and finally got around to it. If you need to trigger a Windows update without using PowerShell, there is a way to do it. In newer versions of Windows 10, usoclient.exe is used to initiate an update scan. However, most of its parameters no longer work except for startinteractivescan. The issue I faced was that it had to be executed as the system account or as the end user in ConfigMgr.

Forrester IT
APRIL 4, 2023
“There’s the door, don’t let it hit you on the way out.” Have you ever been told that or felt that expression when you’ve departed a job?

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

IT Toolbox
APRIL 3, 2023
While the use of edge-to-cloud setups has risen strongly, issues of latency, data security, scalability, and more remain key issues, hindering adoption. The post 4 Challenges of the Edge to Cloud Evolution appeared first on Spiceworks.

Association of Information Technology Professional
APRIL 7, 2023
Leo Guerrero, a high school student, has already earned four CompTIA certifications. See how he is inspiring others a Shadow Ridge High School.

Anoop
APRIL 3, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link]. Read More The post Enroll Android Devices to Android for Work in Intune appeared first on HTMD Community Blog #1 Modern Device Management Guides by Malepati Naren.

Forrester IT
APRIL 6, 2023
We draw the ten important learnings from Walmart’s 2023 fiscal year results.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

IT Toolbox
APRIL 4, 2023
Could smarter signaling security help enterprises move to 5G networks? The post Addressing Signaling Security in the Transition to 5G Networks appeared first on Spiceworks.

Association of Information Technology Professional
APRIL 5, 2023
Many Linux distributions include the nano text editor due to its simplicity and power. Learn to create, edit, save and close files using nano.

Anoop
APRIL 3, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link]. Read More The post SCCM CB Release has Changed 2 Versions per Year | March and September appeared first on HTMD Community Blog #1 Modern Device Management Guides by Vidya M A.

Tech Republic Security
APRIL 3, 2023
Some 43% of employees have been targeted with work-related phishing attacks on their personal devices, says a survey from SlashNext. The post BYOD and personal apps: A recipe for data breaches appeared first on TechRepublic.

Advertisement
You’ve read the PMBOK® Guide several times, taken the certification exam for project managers, passed, and you are now a PMP®. So why do you keep making rookie mistakes? This whitepaper shows 20 of the most common mistakes that young or inexperienced project managers make, issues that can cost significant time and money. It's a good starting point for understanding how and why many PMs get themsleves into trouble, and provides guidance on the types of issues that PMs need to understand.

IT Toolbox
APRIL 4, 2023
Here’s how app developers can prioritize privacy for health apps. The post Developing a Health App? Here’s How to Focus on Privacy appeared first on Spiceworks.

Association of Information Technology Professional
APRIL 6, 2023
With phishing attacks on the rise and human error still the top reason cybercriminals gain access, it’s important that companies keep everyone educated when it comes to fighting back.

Anoop
APRIL 6, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link]. Read More The post Is SCCM Dying? appeared first on HTMD Community Blog #1 Modern Device Management Guides by Vidya M A.

Information Week
APRIL 7, 2023
A network security incident took multiple systems offline. Insight has been limited, but the incident gives Western Digital’s customers and other data storage providers plenty to think about.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

IT Toolbox
APRIL 6, 2023
Explore what measures advertisers can take to reduce carbon footprint. The post Why It’s Time To Prioritize Sustainable Advertising appeared first on Spiceworks.

Association of Information Technology Professional
APRIL 4, 2023
Membership in the CompTIA community opens doors to new potential partners, but also like-minded peers to get answers to questions you won’t get anywhere else.

Tech Republic Cloud
APRIL 3, 2023
Microsoft is making it easier to move existing MongoDB workloads to its Cosmos database. The post New ways to bring MongoDB data and apps to Azure Cosmos DB appeared first on TechRepublic.

Information Week
APRIL 3, 2023
Data protection authorities take swift action following data breach at OpenAI. Observers say CIOs should keep a close watch on regulatory trends as artificial intelligence applications multiply in enterprise use.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

IT Toolbox
APRIL 3, 2023
Cybersecurity simulations and trying to hack your own enterprise can provide interesting insights. The post Five Cybersecurity Simulations to Reduce the Risk of a Painful Data Breach appeared first on Spiceworks.

Association of Information Technology Professional
APRIL 3, 2023
Here are 11 things you should know about IT certifications, before you commit.

Tech Republic Security
APRIL 7, 2023
Joe Burton, CEO of digital identity company Telesign, talks to TechRepublic about how the “fuzzy” realm between statistical analysis and AI can fuel global, fast, accurate identity. The post Company that launched 2FA is pioneering AI for digital identity appeared first on TechRepublic.
Network World
APRIL 4, 2023
Tighter integration between Fortinet's SASE and SD-WAN offerings is among the new features enabled by the latest version of the company's core operating system. FortiOS version 7.4 also includes better automation across its Security Fabric environment, and improved management features. FortiOS is the operating system for the FortiGate family hardware and virtual components, and it implements Fortinet Security Fabric and includes firewalling, access control, Zero Trust, and authentication in addi

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.
Let's personalize your content