6 Ways to Manage Cybersecurity Burnout and Support Teams Better
Information Week
JUNE 13, 2023
Burnout is a contributing factor to the cybersecurity talent shortage. How can this issue be recognized and managed to help teams thrive?

Information Week
JUNE 13, 2023
Burnout is a contributing factor to the cybersecurity talent shortage. How can this issue be recognized and managed to help teams thrive?

TechSpot
JUNE 15, 2023
Experts at cybersecurity firm CyberCX unintentionally put themselves in this exact situation. Old Lenovo L440 laptops the company used in the past had their BIOS "conveniently locked" once the devices were decommissioned. The experts decided to use the computers as test subjects to learn how to break through BIOS passwords.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

IT Toolbox
JUNE 14, 2023
Moving beyond the myths around PBAC to deliver broader security strategies. The post Debunking 5 Myths about Policy-based Access Control appeared first on Spiceworks.

Tech Republic Security
JUNE 13, 2023
The assumptions a business shouldn’t make about its DDoS defenses and the steps it should take now to reduce its likelihood of attack. The post DDoS threats and defense: How certain assumptions can lead to an attack appeared first on TechRepublic.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

IT Toolbox
JUNE 12, 2023
Uncover the keys to employee engagement in the digital-first workplace. The post The Great Disengagement: What Is It and How Can Employers Fix It? appeared first on Spiceworks.

Tech Republic Big Data
JUNE 15, 2023
Learn all about Microsoft Dataverse in this comprehensive overview. Discover its features, benefits, and how it can enhance your data management. The post What is Microsoft Dataverse: A comprehensive overview appeared first on TechRepublic.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.
Tech Republic Security
JUNE 16, 2023
Threat intelligence firm Abnormal Software is seeing cybercriminals using generative AI to go phishing; the same technology is part of the defense. The post AI vs AI: Next front in phishing wars appeared first on TechRepublic.
IT Toolbox
JUNE 15, 2023
Research shows that manufacturers are competing on the quality of CX, not just the quality of their products. The post How Better CX Can Solve Supply Chain Issues in Manufacturing appeared first on Spiceworks.

Anoop
JUNE 15, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link]. Read More The post Account-Driven Apple User Enrolment in Intune – Part 1 appeared first on HTMD Community Blog #1 Modern Device Management Guides by Malepati Naren.
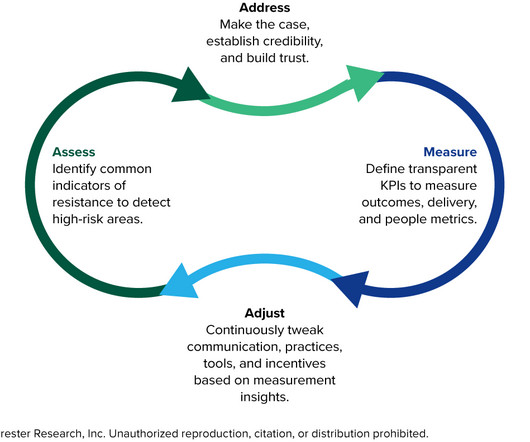
Forrester IT
JUNE 15, 2023
Change resistance can derail be best transformation roadmap. Read this blog to learn about the most common mistakes to avoid.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Tech Republic Security
JUNE 13, 2023
Read the technical details about a new AiTM phishing attack combined with a BEC campaign as revealed by Microsoft, and learn how to mitigate this threat. The post New phishing and business email compromise campaigns increase in complexity, bypass MFA appeared first on TechRepublic.

IT Toolbox
JUNE 14, 2023
Centralized master data management (MDM) solutions offer companies high levels of flexibility and customization. The post Take Control of Your Supply Chain With Master Data Management appeared first on Spiceworks.

Anoop
JUNE 14, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link]. Read More The post First Windows 11 Controlled Feature Rollout Coming Soon appeared first on HTMD Community Blog #1 Modern Device Management Guides by Vidya M A.

Information Week
JUNE 12, 2023
What to look for when reevaluating your team’s tech stack will depend on where your artificial intelligence solution best fits the team’s workflow. Here are a few ideas.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Tech Republic Security
JUNE 15, 2023
FBI, CISA and international organizations released an advisory detailing breadth and depth of LockBit, and how to defend against the most prevalent ransomware of 2022 and (so far) 2023. The post CISA advisory on LockBit: $91 million extorted from 1,700 attacks since 2020 appeared first on TechRepublic.

IT Toolbox
JUNE 15, 2023
Harness the power of language diversity for enhanced innovation, cross-cultural communication, and market adaptation. The post How Language Diversity Boosts Innovation In Tech Teams appeared first on Spiceworks.

Anoop
JUNE 13, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link]. Read More The post Microsoft Defender for Endpoint Portal Walkthrough appeared first on HTMD Community Blog #1 Modern Device Management Guides by Vidya M A.
Information Week
JUNE 12, 2023
Is it time to put out a welcome mat for AI, or is the technology about to pull the rug out from under humanity? Opinions differ, to say the least.

Advertisement
You’ve read the PMBOK® Guide several times, taken the certification exam for project managers, passed, and you are now a PMP®. So why do you keep making rookie mistakes? This whitepaper shows 20 of the most common mistakes that young or inexperienced project managers make, issues that can cost significant time and money. It's a good starting point for understanding how and why many PMs get themsleves into trouble, and provides guidance on the types of issues that PMs need to understand.

Tech Republic Security
JUNE 16, 2023
The study shows attackers are using more bots and doing more sophisticated phishing exploits and server attacks, especially targeting retail. The post Akamai’s new study: Bots, phishing and server attacks making commerce a cybersecurity hotspot appeared first on TechRepublic.

IT Toolbox
JUNE 15, 2023
AWS launched Amazon CodeGuru Security, Amazon Verified Access, Amazon Verified Permissions, and more at AWS re:Inforce 2023. The post AWS re:Inforce 2023: Key Highlights From the Cloud Security Event appeared first on Spiceworks.

Anoop
JUNE 16, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link]. Read More The post MDE Network Protection Policy Deployment using Intune appeared first on HTMD Community Blog #1 Modern Device Management Guides by Vidya M A.

Network World
JUNE 12, 2023
OK, it’s not been a great first half for many companies, from end users to vendors and providers. The good news is that users sort of believe that many of the economic and political issues that have contributed to the problem have been at least held at bay. There’s still uncertainty in the tech world, but it's a bit less than before. Most of the companies I’ve talked with this year have stayed guardedly optimistic that things were going to improve.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Information Week
JUNE 15, 2023
AI collaboration across corporate boundaries can greatly accelerate innovations in data science, AI model development, and applying AI to use cases in real world situations -- here are some examples of how some organizations are making it work.

IT Toolbox
JUNE 15, 2023
Can business transformation and ESG goals be attained together? The post 5 Keys to Unlock Healthy ESG and Business Transformation appeared first on Spiceworks.

Anoop
JUNE 12, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link]. Read More The post Latest Method to Install Intune Company Portal App for Windows Devices appeared first on HTMD Community Blog #1 Modern Device Management Guides by Jitesh Kumar.

Tech Republic Security
JUNE 12, 2023
Google’s ChromeOS is not just for Chromebooks. Thomas Riedl, the Google unit’s head of enterprise, sees big growth opportunities for the OS where security and versatility matter most. The post Google’s ChromeOS aims for enterprise with security and compatibility appeared first on TechRepublic.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Information Week
JUNE 15, 2023
Generative AI is now automating the creation of written content, but the new technology also requires guardrails, experts say.

IT Toolbox
JUNE 14, 2023
The FTC filed a preliminary injunction and temporary restraining order to block Microsoft’s Activision Blizzard deal. The post FTC Stalls Microsoft’s $69 Billion Acquisition of Activision appeared first on Spiceworks.

Anoop
JUNE 14, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link]. Read More The post How to Troubleshoot Microsoft Enterprise SSO Plug-in on macOS using Intune appeared first on HTMD Community Blog #1 Modern Device Management Guides by Snehasis Pani.

TechSpot
JUNE 16, 2023
Among the many changes, the new rules would require batteries in consumer devices like smartphones to be easily removable and replaceable. That's far from the case today with most phones, but that wasn't always the case.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.
Let's personalize your content