How to Gain Control Over Shadow Analytics
Information Week
OCTOBER 3, 2023
Are unauthorized analytical tools placing your enterprise at risk? Learn how to detect and remove shadow analytics without disrupting productivity.

Information Week
OCTOBER 3, 2023
Are unauthorized analytical tools placing your enterprise at risk? Learn how to detect and remove shadow analytics without disrupting productivity.

IT Toolbox
OCTOBER 4, 2023
Align cybersecurity with your board’s vision. Learn how CISOs can bridge gaps and secure crucial support for robust cyber initiatives. The post How CISOs Can Build Support for Cybersecurity on Their Boards appeared first on Spiceworks.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Tech Republic Cloud
OCTOBER 4, 2023
Apptio Asia-Pacific General Manager Pete Wilson says growing IT financial literacy in local enterprises is helping IT teams resist cost-cutting pressure and tie spending to business growth.

Forrester IT
OCTOBER 3, 2023
Do you understand generative AI? Forrester’s data shows that 54% of AI decision-makers believe their organization’s executive team is “very familiar” with it — but we’ve observed widespread misunderstandings among execs of what it is, how it works behind the curtain, and what it can do.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Information Week
OCTOBER 2, 2023
With passage of the Delete Act, data brokers now face some of the toughest requirements yet. But does the new law have teeth?

IT Toolbox
OCTOBER 2, 2023
The era of the hybrid cloud and how to lead a successful migration. The post Why Choose the Hybrid Cloud Over Full Cloud Migration appeared first on Spiceworks.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Forrester IT
OCTOBER 6, 2023
Are we right to expect the same superpowers and natural dialogue that J.A.R.V.I.S., the AI assistant, brings to Iron Man as what generative AI (genAI) will bring to CRM?
Tech Republic Security
OCTOBER 6, 2023
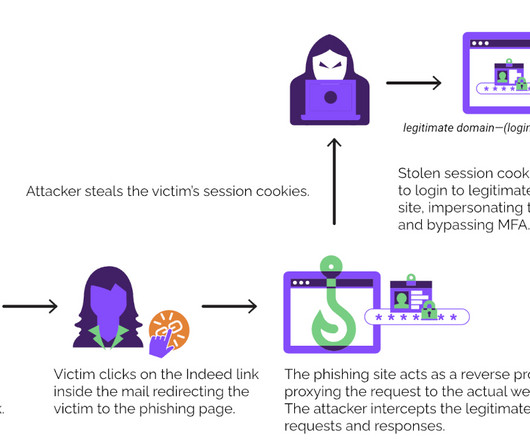
Microsoft, the Dark Web and the name John Malkovich all factor into this EvilProxy phishing attack. The good news is there are steps IT can take to mitigate this security threat.

IT Toolbox
OCTOBER 3, 2023
The suit claims that Elon Musk’s company uses the X mark to promote services identical to that of X Social Media. The post Elon Musk’s X Faces Legal Hurdle With Trademark Lawsuit From Marketing Firm appeared first on Spiceworks.

Anoop
OCTOBER 4, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link] The post Schedule Scans with Microsoft Defender for Endpoint on macOS from Intune appeared first on HTMD Community Blog #1 Modern Device Management Guides by Jitesh Kumar.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
Forrester IT
OCTOBER 3, 2023
Mobile banking matters more than ever in the US and Canada. Online banking usage is trending down as mobile banking usage and engagement continue to rise. In mobile banking channels, customers demand a widening set of features and services — and these mobile experiences have a major impact on brand perceptions and preferences.

Information Week
OCTOBER 2, 2023
With businesses often confused about what artificial intelligence is and can do for an organization, the role of defining AI falls to IT and data professionals.

IT Toolbox
OCTOBER 5, 2023
Tech revolutionizing construction management for faster, cost-efficient projects worldwide. The post Construction Management Revolution: The Power of Innovative Tech appeared first on Spiceworks.

Anoop
OCTOBER 3, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link] The post Configure New Managed Settings in macOS Catalogue using Intune 2309 release or later appeared first on HTMD Community Blog #1 Modern Device Management Guides by Snehasis Pani.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Forrester IT
OCTOBER 6, 2023
Generative AI continues to be the topic du jour, as businesses race to understand the technology for fear of being left behind. But what about consumers? Forrester is closely tracking this. I’ll be taking you through how consumers know, feel, and use Generative AI every quarter.

Information Week
OCTOBER 3, 2023
As the potential use cases for AI come into shape, so do several ethical issues. Health care providers, patients, AI developers and regulators all have a stake in ethical use of AI, but how will those ethics be defined?

IT Toolbox
OCTOBER 3, 2023
Smart manufacturing needs smarter OT cybersecurity strategies. The post Why Smart Manufacturing Needs Smarter Cybersecurity appeared first on Spiceworks.

Anoop
OCTOBER 3, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link] The post Best way to Manage SCCM Client on Windows Server Core Machines appeared first on HTMD Community Blog #1 Modern Device Management Guides by Sujin Nelladath.

Advertisement
You’ve read the PMBOK® Guide several times, taken the certification exam for project managers, passed, and you are now a PMP®. So why do you keep making rookie mistakes? This whitepaper shows 20 of the most common mistakes that young or inexperienced project managers make, issues that can cost significant time and money. It's a good starting point for understanding how and why many PMs get themsleves into trouble, and provides guidance on the types of issues that PMs need to understand.

Forrester IT
OCTOBER 2, 2023
We have a national day or month for just about everything. Some of my personal favorites include National IPA Day (first Thursday in August), National Waffle Day (August 24), National Rescue Dog Day (May 20), and National Insider Threat Awareness Month (September).

Information Week
OCTOBER 6, 2023
The cyberattack raises concerns of physical security at the Department of Homeland Security, and a possible government shutdown prompts more cybersecurity concerns.

IT Toolbox
OCTOBER 4, 2023
Discover how AI-driven intelligent IAM is an essential component of your long-term cybersecurity strategy. The post How Can AI-powered Solutions Enhance Identity Security? appeared first on Spiceworks.
Anoop
OCTOBER 3, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link] The post FIX Restricted Access to FQDN and IP Hyperlinks Issues in Outlook appeared first on HTMD Community Blog #1 Modern Device Management Guides by Vidya M A.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Forrester IT
OCTOBER 5, 2023
Text analytics is a peculiar software market segment. Vendors typically have a main offering that heavily relies on text mining and analytics, but they rarely position themselves explicitly as “text analytics platforms.
Information Week
OCTOBER 6, 2023
Patch now: The Atlassian security vulnerability appears to be a remotely exploitable privilege-escalation bug that cyberattackers could use to crack collaboration environments wide open.

IT Toolbox
OCTOBER 5, 2023
How can IoT improve cars and our relationship with them? The post Enjoy the Ride: Cars and Drives Are Better With the IoT appeared first on Spiceworks.

Tech Republic Security
OCTOBER 3, 2023
It doesn’t matter whether your organization is a huge multinational business enterprise or a one-person operation. At some point, your computer networks and systems will be attacked by someone with criminal intent. Cybersecurity attacks, in all their various forms, are inevitable and relentless. This quick glossary from TechRepublic Premium explains the terminology behind the most.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Forrester IT
OCTOBER 3, 2023
Does your organization span regions, lines of business and brands? That makes scaling a customer experience measurement program more challenging; you need to balance consistency and oversight with adaptation and localization.

Information Week
OCTOBER 3, 2023
A European report says greenwashing is on the rise at companies in America and Europe -- especially in the banking and financial services sectors. “Social washing” is also increasing.

IT Toolbox
OCTOBER 4, 2023
Harmonize SASE with existing networks. Gradual migration strategy maximizes innovation and financial resources. The post 5-step Iterative Strategy for Successful SASE Transformation appeared first on Spiceworks.

Anoop
OCTOBER 4, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link] The post Fix Windows Autopilot Device Registration Errors 802 806 808 640 appeared first on HTMD Community Blog #1 Modern Device Management Guides by Vidya M A.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.
Let's personalize your content