2024 Security Recommendations: Tackle Change Head On
Forrester IT
MARCH 6, 2024
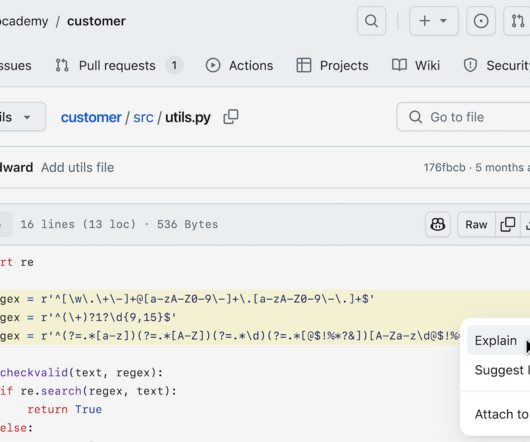
We recently published the Top Recommendations For Your Security Program, 2024 report for CISOs and other senior cybersecurity and technology leaders. The theme for our annual recommendations report this year centers around the importance of anticipating and leading change. Changing threats.


















































Let's personalize your content