Google reports on a company selling spyware for Chrome, Firefox, and Windows Defender
TechSpot
DECEMBER 1, 2022
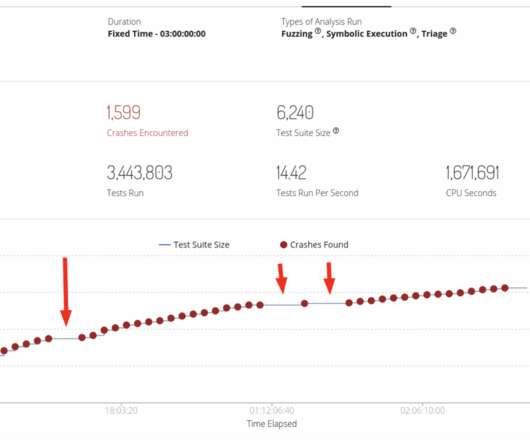
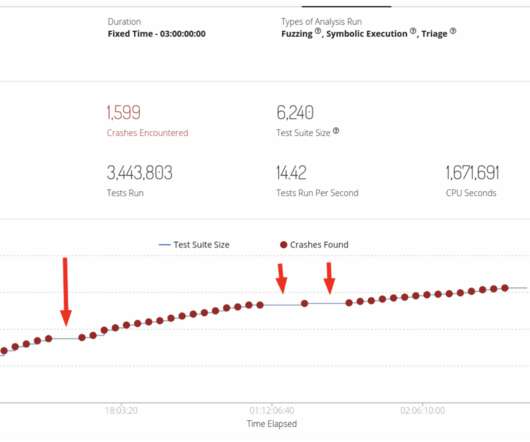
Google's Threat Analysis Group (TAG) reports that a Barcelona company sold spyware exploiting Chrome, Firefox, and Windows Defender vulnerabilities to conduct contract surveillance on target PCs.













































Let's personalize your content