Using X.509 Certs for DID Provenance
Phil Windley
APRIL 25, 2024
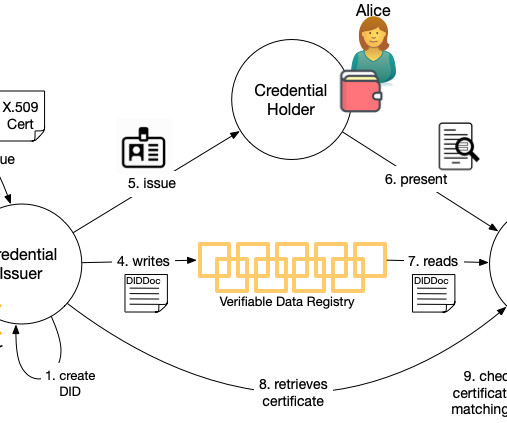
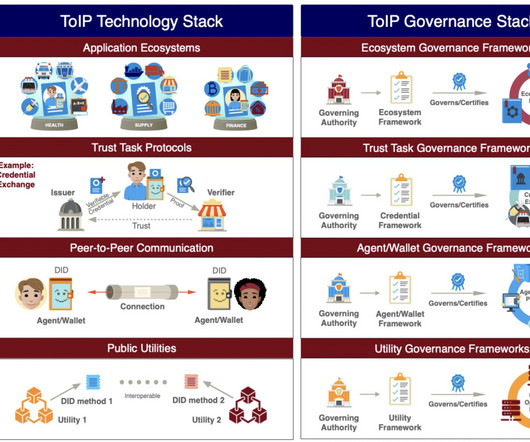
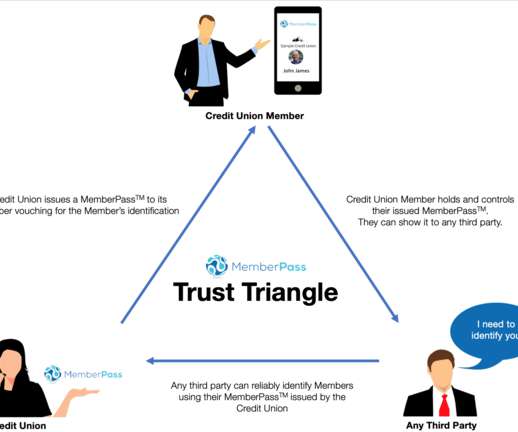
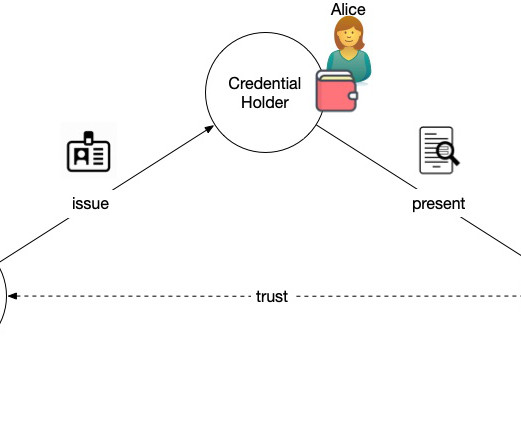
They don't, however, tell them whether they can trust the issuer. That might be all the evidence they need to determine whether to trust the entity. 509 certificates is that there are already many trusted X.509 Summary: The abundance of X.509 At the most recent Internet Identity Workshop , Drummond Reed gave a session on how X.509








































Let's personalize your content