With all of what has happened this past year, I think we’ve finally killed off the idea of the perimeter as a viable defense metaphor. But the idea isn’t completely dead – it’s mostly dead. If it was completely dead, there would only be one thing left to do: Go through the firewall’s logs and search for loose change. I just couldn’t help myself with the Princess Bride reference!
The cold hard truth is that zero trust is very much on its way. As part of the long goodbye to the firewall-first approach, we’ve been hearing quite a bit about how cybersecurity pros use various technologies and practices, including automated end-point detection and response, user behavior analytics, connection monitoring and so forth. That’s certainly part of the equation, but it doesn’t really put zero trust in a technical context with the cybersecurity technologies and processes that already exist.
The zero trust approach is quickly gaining ground – and cybersecurity pros are talking about it. There’s already great information out there about the four pieces of zero trust, And how the cloud and zero trust are, in many ways, meant for each other. I’d like to add even more about the nature of zero trust on a technical level – which some find a bit daunting. After all, there’s no single, poster child zero trust application, procedure or product. From a technical perspective, there are at least six.
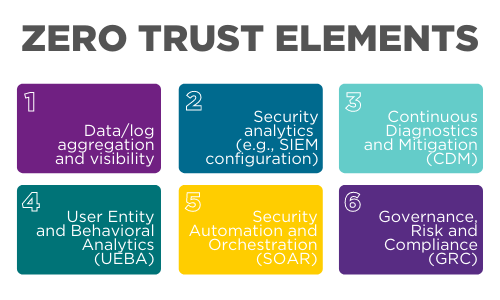
Figure 1: Zero trust elements
Understanding the Zero Trust Strategy
Let me explain these six approaches in a bit more detail.
- Data and log aggregation: The ability to gather not only log files, but also packet-capture information, as well as data feeds. These are three very separate elements, because they originate from very different places. Log files come from servers and edge resources. Capture information comes from the network wire. Data feeds come from cloud services, as well as cyber threat feeds. Aggregation in a post-modern network means you’re creating a huge data lake that you can then strain for cybersecurity trends.
- Cybersecurity analytics: Someone needs to analyze the trends found in your aggregated data. An analyst does this by leveraging information from various resources, including security information and event management (SIEM) tools.
- Continuous diagnostics and mitigation: A zero trust network does more than scan a system when it logs in. A zero trust network continually evaluates the state of a system, including its user and all of the processes launched during a session.
- User behavior analytics: It has become a cliché for cyber pros to blame end users. But user behavior analytics overrides this cliché, and are useful and time-tested. For those who really want to use an acronym, I’ve often seen this practice called user entity and behavioral analytics (UEBA). I’m less fond of this acronym, because part of behavior analytics is looking at various computer and cloud processes, not just those associated with a particular end user. It’s a vital element, because it helps organizations gain a laser-like focus on end users, and all things associated with them.
- Security automation and orchestration (SOAR) and threat hunting: Timely response can only occur when it’s properly automated. So much has been written about the ability for (post)modern platforms to automatically respond to changes in the environment. When it comes to zero trust, however, we need workers that can automate key processes. This is a heuristic process that isn’t enabled by an appliance or piece of software. It’s a capability that is honed by qualified cybersecurity professionals who hunt for threats, then automate networks to counter them.
- Governance, risk and compliance (GRC): This sixth element is the one that most folks leave out, usually because techies tend to talk in terms of tools, rather than policy. Yet governance, including compliance, is vital. This is why GRC has become one of the more-discussed acronyms over the past year. Yet, most people tend to not include it under the banner of zero trust.
Countering the Starbucks Factor with Zero Trust
Some folks find this zero trust talk a bit confusing, because they’ve been taught that a well-monitored virtual private network (VPN) is a viable solution. But we’ve long seen the problem with VPNs – even before COVID-19. In late 2020, I spoke at length with John Rouffas, chief information security officer (CISO) at Bink, a fintech company, about his struggles to convince his leaders to move to a zero trust environment. He told me that he really made his CEO understand the importance of zero trust when he pointed out that, “Everybody’s connecting from Starbucks with an infected end-point device.”
This statement helped his CEO truly understand how they could avoid VPN solutions, and eliminate – or at least moderate – the traditional binary inside/outside cybersecurity model. This is important, because even though a VPN creates a nice, encrypted tunnel for traffic, it also creates a problem: That tunnel allows infected endpoints access into the rest of your network. This is why we need several different coordinated technologies to implement zero trust.
Zero Trust and Zombie Flicks: Know When Something Takes a Turn For the Worse
Zero trust does more than help resolve the traditional inside/outside approach to cybersecurity. It also helps avoid assuming the current state of a particular device or process. With the supply chain attacks we’ve seen recently, know that a trusted device, process or data stream can, effectively, become a threat. For example, I’m a fan of all sorts of movies. But lately, I’ve found zombie flicks especially interesting. Maybe the COVID-19 outbreak has influenced my viewing choices. Or, maybe it’s the increasing frequency of DDoS and ransomware attacks we’ve seen over the last year. I’ll let you decide.
But in a semi-absurd way, movies like 28 Days Later, Zombieland, Night of the Living Dead, and Shaun of the Dead help shed light on the key zero trust concept: You simply can’t assume a trusted process, end point or user will remain trustworthy. One of the truisms of a good zombie movie is that you never know when a trusted friend will become a bloodthirsty, flesh-eating zombie. One of the true weaknesses of traditional networking models is that they never took that essential zombie truism into account.
IT pros implementing today's post-modern IT environment pretty much take that truism into account. Much like living in a zombie movie, they recognize that they really don’t know if a particular process, data stream, software update or communication will somehow turn on them. They then act accordingly. Instead of hoping that things don’t change for the worse, they assume a worst-case scenario. The result? A need for constant assessment, automation and segmentation – the very elements that a zero trust network can provide.
CompTIA is here to support you throughout your IT career. Get free resources, career advice, and special offers on CompTIA training and certifications!

