Using X.509 Certs for DID Provenance
Phil Windley
APRIL 25, 2024
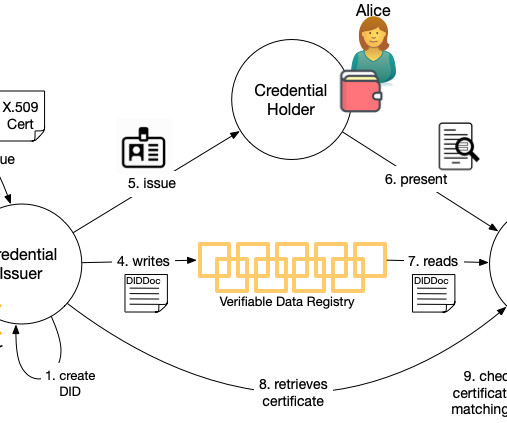
509 certificate authorities who already perform identity proofing for businesses provides a rich resource that can be leveraged to boot the verifiable data ecosystem. 509 certificates could help with this. The first step, like always, is to resolve the DID and retrieve the DIDDoc that associates keys and endpoints with the DID.


















































Let's personalize your content