Living with COVID-19 means we’ve been inundated with monitoring, observation isolation and contact tracing. As controversial as these topics might be, I’ve noticed that when it comes to cybersecurity and applications, the idea of monitoring and the concept of observability have become extremely important.
Last year, CompTIA’s State of Cybersecurity 2020 report found that security monitoring was a “top-of-mind” concern, as shown below.
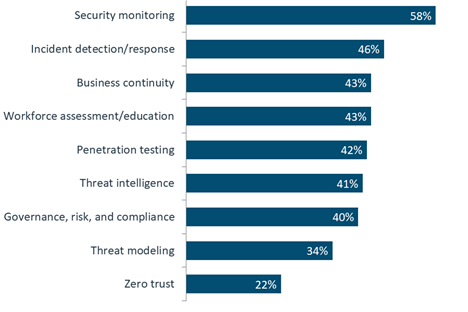
Figure 1: Top cybersecurity skills, including monitoring
And this year, the State of Cybersecurity 2021 report doubled down on the importance of monitoring, showing how important analytics has become to hiring managers when it comes to cybersecurity.
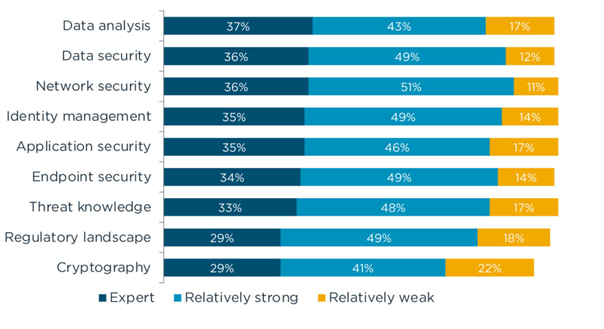
Figure 2: Cybersecurity analytics and monitoring from 2021 to 2022
Monitoring involves using tried and tested tools and best practices, such as intrusion detection, advanced logging and Security Information and Event Management (SIEM) platforms. Today, organizations are doing all they can to hire qualified cybersecurity analysts, one of the fastest-growing, security-oriented job roles today.
Observability: The Next Level?
Typical monitoring involves passive listening to host and network data using tools such as router logs, and applications like Snort, Zeek and Suricata, SIEM tools and other log and data-oriented activities. But, to get even more context and delve more deeply into how applications work, there seems to be a relatively new concept: Observability. The two practices are related, but not identical. Think of it this way: Monitoring is kind of like using Google Maps – it does a great job of giving you a general idea of the lay of the land. Observability is more detailed – kind of like Google Street View, or an augmented reality application that allows you to see exactly what is going on at a given time.
Why Is Observability Important?
From a cybersecurity analyst’s perspective, it’s not enough to implement more passive monitoring tools. We need applications, cloud services and edge devices to actively contribute information about how they are running in real-time. This is because hackers are increasingly attacking applications to obtain user credentials and other sensitive information.
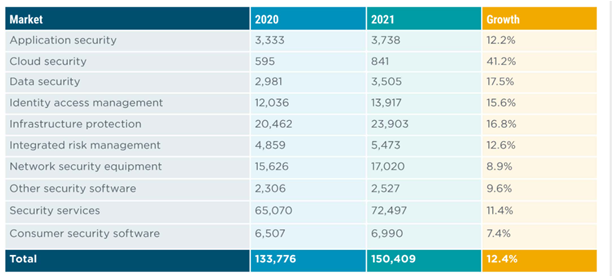
Figure 3: The CompTIA State of Cybersecurity 2021 report, showing cyber spending increases on application, data and cloud security
It’s one thing to monitor how things are behaving. But suppose you could have a developer build functionality right into the application so that it continually reports how it is behaving?
How We Define Observability
Observability is the ability of an application or device to proactively report its overall condition. For example, most of us have experienced that wonderful moment when your car’s “check engine” light suddenly decides to brighten up your dashboard – and your day. We’ve also experienced a trip to the mechanic, who then connects her computer to your car. The two computers talk to each other, and then your mechanic diagnoses the problem.
This is an example of observability: Today’s cars have code written into their computers and applications that throw off codes, informing your mechanic about a specific problem. The thinking is that access to these real-time codes eliminates the need to guess what’s wrong with your car. The codes tell you exactly what’s happening
In the DevSecOps world, observability is where you – the security professional – work with a developer to create applications that contain embedded code. This code allows IT and cybersecurity professionals to look into how these applications are performing in real-time. In fact, observability implies the ability for the application to report exactly how it is behaving. This is a pretty cool idea. Instead of having to deploy end user behavior and analytics (UEBA) tools and hope for the best, you have applications proactively reporting their status. Imagine how useful observability data would be if it was routed through machine learning (ML) analytics tools. These tools could more easily identify potential security and outage issues.
Figure 4, below, shows a simple idea about how observability can work. An application contains real-time information that informs members of a security operations center (SOC) about its current state.
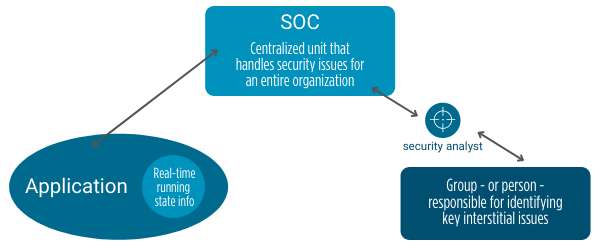
Figure 4: Applications providing real-time running information to a SOC
Putting Observability to Work
To make observability a reality, cybersecurity professionals work closely with application developers. Together, they embed code and functionality into an application. This code operates according to four principles:
- Logging: These are the raw materials – the facts – coming from various devices, from the edge, all the way through end points, applications and application programming interfaces (APIs). This is a primary element – one of the reasons many will see observability as “monitoring on steroids.”
- Metrics: This is more than the typical log files that a device or application generates. This information includes the CPU usage, available (or consumed) memory and response time.
- Trace: This is the path an application, or process, has to go down to fulfill a particular request.
- Visualization: This is the ability to turn logs, metrics and traces into a useful narrative. The goal is to visualize actionable information. Sometimes, this involves the use of machine learning or other adjuncts to provide more context and make recommendations.
Figure 5: The four principles of observability
The Benefits of Observability
The promise behind the activity of tracing – and observability in general – is that it is possible to more quickly identify attacks in progress, and bring more context to the cybersecurity professional. Of course, it won’t automate and solve everything. In the same way that you need a good mechanic to read the codes provided by a car, we’ll need good cybersecurity analysts to draw the right conclusions.
Any time we can use a tool – such as observability – to add more context and intelligence to how applications are running, it’s always worthwhile. With observability, cybersecurity professionals can move closer to the goal of AI-driven predictive analysis and pre-correlated, useful information.
CompTIA Cybersecurity Analyst (CySA+) covers monitoring and observability. Get the skills you need with a free trial of CertMaster Learn + Labs for CySA+.

