OAuth and Fine-grained Access Control
Phil Windley
APRIL 18, 2023
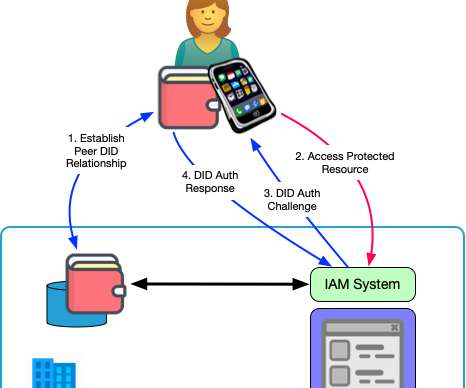
Policy-based Access Control (PBAC) systems, on the other hand, were built for this kind of permissioning. As I wrote in Not all PBAC is ABAC , your app design and how you choose to express policies make a big difference in the number of policies you need to write. Tags: identity access+control oauth abac













Let's personalize your content