Coronavirus Cybercrimes: Are These the Lowest?
Information Technology Zone Submitted Articles
SEPTEMBER 21, 2020
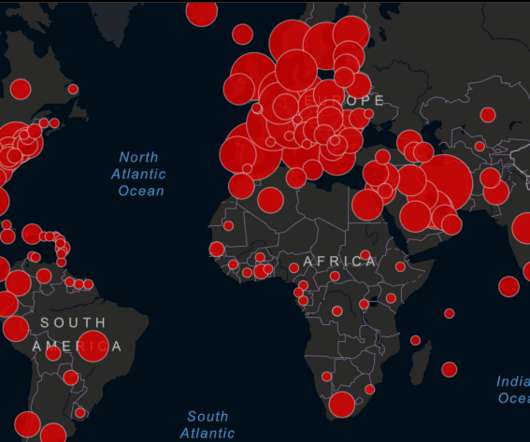
The coronavirus and pandemic cyberattacks.
Information Technology Zone Submitted Articles
SEPTEMBER 21, 2020
The coronavirus and pandemic cyberattacks.

Information Technology Zone Submitted Articles
MAY 24, 2020
The issue is mired in complexity
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Network World
DECEMBER 15, 2020
A group believed to be Russia's Cozy Bear gained access to government and other systems through a compromised update to SolarWinds' Orion software. Most organizations aren't prepared for this sort of software supply chain attack.

Forrester IT
DECEMBER 22, 2020
(Written with Benjamin Corey, senior research associate at Forrester) Telehealth (virtual care) usage has skyrocketed during the pandemic. When you roll back the tape a few months, healthcare providers were able to (very quickly) stand up virtual care capabilities without having to go through the intensive HIPAA compliance protocols required in the healthcare industry.

Advertisement
With its unparalleled flexibility, rapid development and cost-saving capabilities, open source is proving time and again that it’s the leader in data management. But as the growth in open source adoption increases, so does the complexity of your data infrastructure. In this Analyst Brief developed with IDC, discover how and why the best solution to this complexity is a managed service, including: Streamlined compliance with some of the most complex regulatory guidelines Simplified operations, li

SecureWorld News
OCTOBER 13, 2020
FBI sting reveals a ransomware gang is bribing employees to help launch cyber attacks against their own employers. Details of a foiled ransomware attack.

Anoop
DECEMBER 24, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s read and learn for this holiday season. The following table gives you the option to download ConfigMgr eBooks and some Intune eBooks for free. Hope these help to have a better understanding of Windows 10, Intune, and SCCM. Apart from all these eBooks, you can start learning new technologies using Microsoft Learn TV.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Tech Republic Security
DECEMBER 17, 2020
The COVID-19 crisis enabled scammers to take advantage of the guileless, as bad actors were able to extract personal information from targets, according to a new report from First Orion.
Tech Republic Cloud
DECEMBER 11, 2020
At Friday's re:Invent 2020 conference event, the e-commerce giant revealed that by 2025 it will invest "hundreds of millions" to help 29 million people worldwide to develop tech skills.

The Verge
DECEMBER 29, 2020
Boston Dynamics’ Atlas and Spot robots can do a lot of things: sprinting , gymnastic routines , parkour , backflips , open doors to let in an army of their friends, wash dishes , and (poorly) get actual jobs. But the company’s latest video adds another impressive trick to our future robotic overlords’ repertoire: busting sick dance moves. The video sees Boston Dynamics entire lineup of robots — the humanoid Atlas, the dog-shaped Spot, and the box-juggling Handle — all come together in a bopping,

GeekWire
DECEMBER 28, 2020
(BigStock Photo). “Microsoft, FireEye, and the U.S. Treasury department have been hacked in the SolarWinds attacks.”. This statement is true but doesn’t tell the whole story accurately. It’s true because by most people’s understanding, these organizations have been hacked. But it doesn’t tell the whole story accurately because each of these organizations has had different impacts with different levels of severity from “the hack.” A good example of why this matters is how we talk abou

Advertisement
The complexity of financial data, the need for real-time insight, and the demand for user-friendly visualizations can seem daunting when it comes to analytics - but there is an easier way. With Logi Symphony, we aim to turn these challenges into opportunities. Our platform empowers you to seamlessly integrate advanced data analytics, generative AI, data visualization, and pixel-perfect reporting into your applications, transforming raw data into actionable insights.

Venture Beast
DECEMBER 27, 2020
GUEST: Last week, on the heels of DeepMind’s breakthrough in using AI to predict protein-folding came the news that the UK-based AI company is still costing its parent company Alphabet Inc hundreds of millions of dollars in losses each year. A tech company losing money is nothing new. The tech industry is replete with examples of companies who burn… Read More.

Information Technology Zone Submitted Articles
MAY 19, 2020
IT and business leaders will run into some false notions about artificial intelligence and machine learning and what each one can do. Here's how to explain the truth on AI vs. ML.

Gizmodo
DECEMBER 22, 2020
If you’re reading this, you might have read the juicy piece that Elle dropped this weekend chronicling how a former Bloomberg reporter torched her entire career after falling for the longtime subject of her reporting— professional-tool -turned-convicted-securities-fraudster Martin Shkreli. And if you know about that… Read more.

TechSpot
DECEMBER 12, 2020
As a corporation, it's Nvidia's prerogative to decide on the reviewers it chooses to collaborate with. However, this and other related incidents raise serious questions around journalistic independence and what they are expecting of reviewers when they are sent products for an unbiased opinion. As an independent tech publication, we've.

Advertisement
Adding high-quality entity resolution capabilities to enterprise applications, services, data fabrics or data pipelines can be daunting and expensive. Organizations often invest millions of dollars and years of effort to achieve subpar results. This guide will walk you through the requirements and challenges of implementing entity resolution. By the end, you'll understand what to look for, the most common mistakes and pitfalls to avoid, and your options.

SecureWorld News
SEPTEMBER 21, 2020
Major fines and major findings in the Capitol One data breach investigation. Here is what a U.S. regulatory agency revealed about the bank data breach.

Anoop
DECEMBER 31, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s find out the top 10 ConfigMgr Intune Videos of 2020 on the basis of popularity & total views. Thank you much for the support during the special year 2020. And all the very best for 2021! Don’t forget to subscribe and share if you like some of these videos.

Information Week
DECEMBER 22, 2020
Artificial intelligence and automation were key tools in the IT enterprises' pandemic war effort in 2020. Here's how they will continue to change the game in every organization in 2021.
Tech Republic Security
NOVEMBER 20, 2020
IBM, Honeywell, and Intel are just three companies leading the way in building quantum machines as well as the algorithms and controls to run them. Learn about possible business use cases for quantum.

Advertiser: Procom Services
From streamlining the job search process to efficiently navigating the influx of applications, AI-powered tools can revolutionize your recruitment efforts. By combining the efficiency of AI with the expertise of experienced recruiters, you can identify the ideal candidates who not only possess the necessary skills but also align with your company culture.

Tech Republic Cloud
DECEMBER 7, 2020
Commentary: The HPC market has struggled to modernize with cloud, but startups like Rescale may be able to change this.

The Verge
DECEMBER 25, 2020
Illustration by Alex Castro / The Verge. Tesla’s new holiday update will finally give people the ability to use a new Boombox mode, which can broadcast custom audio on the outside of the car (hence the name). As is common with new Tesla features, Boombox combines real utility with lowbrow humor: owners can use fart and goat sounds in lieu of normal, boring honking sounds car horns usually make.

GeekWire
DECEMBER 28, 2020
Amazon’s Spheres, with the Amazon Day 1 tower and Seattle’s iconic Space Needle in the background. (GeekWire Photo / Kurt Schlosser). Techies are apparently leaving Silicon Valley. The pandemic has sparked what some describe as an “exodus” of tech companies, employees, and investors who are relocating to Austin, Miami, Reno, Madison, and other metros for a myriad of reasons.
Venture Beast
DECEMBER 17, 2020
Discord has raised another $100 million in funding as the instant messaging app popularized by gamers has now hit 140 million monthly active users. Read More.

Speaker: Kat Conner
The challenge of delivering the right product at the right time while aligning with strategic objectives is more pressing than ever. Product management is evolving and gaining greater recognition as the means to creating this connection. Join our upcoming webinar and learn how to streamline your product development processes, infuse product thinking across the organization, and bridge the gap between vision and delivery.

Information Technology Zone Submitted Articles
OCTOBER 19, 2020
Too much information and not enough time. This, and the cost of labor, is why machines have been at the forefront of cyber defense for almost 50 years. It is also why new breakthroughs in software development, neural networks, machine learning and artificial intelligence (AI) are constantly harnessed by providers and consumers of threat intelligence.

Gizmodo
DECEMBER 21, 2020
Her life was short. Scientists estimate she lived for about six or seven weeks in the underground den, before it collapsed around her. This tragedy and the permafrost that preserved her body are the reasons we know of this wolf pup’s existence approximately 57,000 years later. Zhùr, or ‘wolf’ in the Hän language, is… Read more.

TechSpot
DECEMBER 7, 2020
Working with academic experts, Royal Panda developed a four-part quiz that measured verbal intelligence, logical reasoning, mathematical ability, and visual reasoning. Before taking the tests, administrators asked respondents to fill out a demographics questionnaire to determine their gaming, computing, and mobile preferences.

Dataconomy
DECEMBER 18, 2020
The saying “knowledge is power” doesn’t just apply to individuals but also businesses. While individuals can learn from books and life lessons, businesses need a tool to gather market insights. This is where online data collection comes in. It is one of the best tools because it provides up-to-date and. The post Open and free online data collection will fuel future innovations appeared first on Dataconomy.

Speaker: Maher Hanafi, VP of Engineering at Betterworks & Tony Karrer, CTO at Aggregage
Executive leaders and board members are pushing their teams to adopt Generative AI to gain a competitive edge, save money, and otherwise take advantage of the promise of this new era of artificial intelligence. There's no question that it is challenging to figure out where to focus and how to advance when it’s a new field that is evolving everyday. 💡 This new webinar featuring Maher Hanafi, VP of Engineering at Betterworks, will explore a practical framework to transform Generative AI pr

Anoop
DECEMBER 11, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Let’s try to understand How to deploy Microsoft Store Apps Using ConfigMgr. Microsoft Store for Business gives opportunity organizations to automatically sync Microsoft store apps and make them available for ConfigMgr admins. Once the Microsoft store for business application is synced with Configuration Manager, you can create a Microsoft Store application in the admin console […].

Information Week
DECEMBER 28, 2020
We will never rid ourselves of all our biases overnight. But we can pass on a legacy in AI that is sufficiently aware of the past to foster a more just and equitable society.
Tech Republic Security
DECEMBER 10, 2020
From Apple to Google to Toyota, companies across the world are pouring resources into developing AI systems with machine learning. This comprehensive guide explains what machine learning really means.

Vox
DECEMBER 14, 2020
Sandra Lindsay, a nurse at Long Island Jewish Medical Center, receives the first Pfizer-BioNTech Covid-19 vaccine at Long Island Jewish Medical Center in Queens, New York. | Mark Lennihan / POOL / AFP. A Trump administration plan to use celebrities has been scrapped, but other vaccine education campaigns are turning to influencers to boost Covid-19 inoculation.

Speaker: Laura Noonan, Chief Revenue Officer at CallFinder + Angie Kronlage, Director of Program Success at Working Solutions + April Wiita, Vice President of Program Success at Working Solutions
Are you still manually reviewing calls? 🤔 It's time for a change! The traditional method of manual call monitoring is no longer cutting it in today's fast-paced call center environment. Industry experts Angie Kronlage and April Wiita from Working Solutions are here to explore the power of innovative automation to revolutionize outdated call review processes!
Let's personalize your content