Von Neumann Architecture vs. Harvard Architecture: A Detailed Comparison
IT Toolbox
MARCH 26, 2024
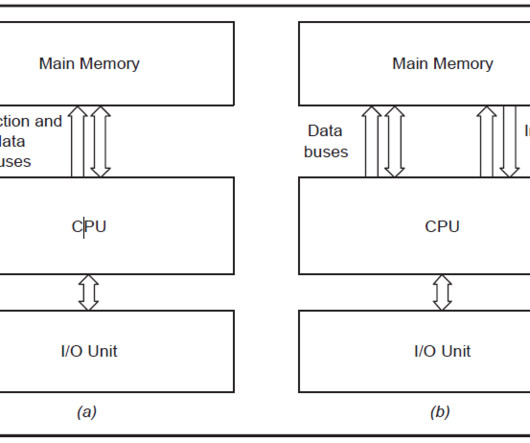
Von Neumann architecture is the foundation for most modern computers, while Harvard architecture offers an alternative design for specific applications. This article provides a detailed comparison of the two most popular computer architectures.













































Let's personalize your content