A Hitchhiker?s Guide to Windows Containers
Linux Academy
MAY 15, 2020
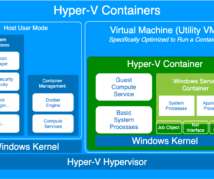
First, I want to acknowledge that there is a big difference between Linux and Windows containers. Linux containers have been around for many decades, in one form or another. The Linux operating system naturally lent itself to taking advantage of containers using namespaces and control groups (cgroups). Why Windows?













Let's personalize your content