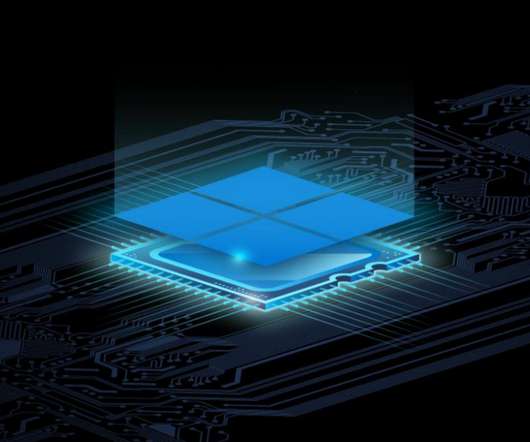
Microsoft Pluton is a new processor with Xbox-like security for Windows PCs
The Verge
NOVEMBER 17, 2020
We shipped the Xbox which has this physical attack protection, so people can’t just hack it for games etc,” explains David Weston, director of enterprise and OS security at Microsoft. “We That means features like BitLocker encryption or Windows Hello authentication will transition over to using Pluton in the future. so you just get it.”




















Let's personalize your content