A Disturbing Trend in Ransomware Attacks: Legitimate Software Abuse
CIO Business Intelligence
JULY 18, 2023
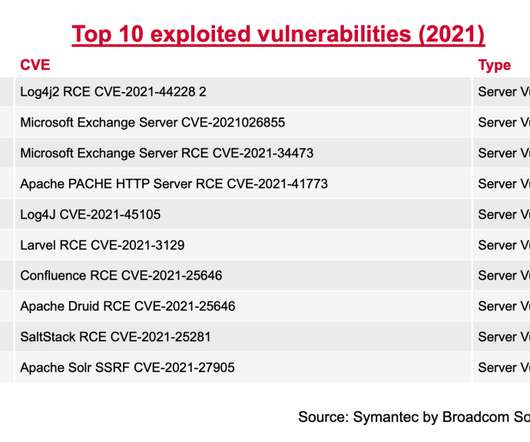
For example, the particularly heavy use of legitimate software tools in ransomware attack chains has been notable in recent times. In fact, we rarely see a ransomware attack that doesn’t use legitimate software. Ransomware actors, like threat actors in general, are abusing legitimate software for a number of reasons.























Let's personalize your content