Using X.509 Certs for DID Provenance
Phil Windley
APRIL 25, 2024
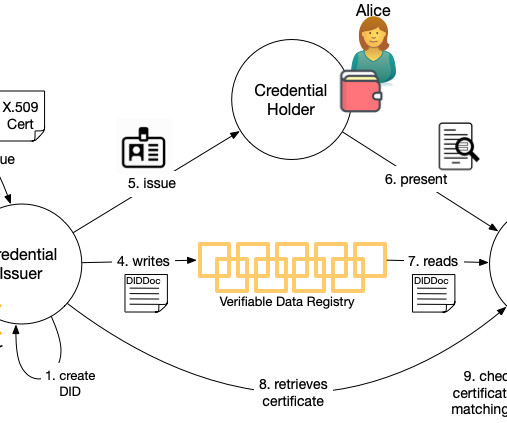
At the most recent Internet Identity Workshop , Drummond Reed gave a session on how X.509 509 certificate for that endpoint, including in the application the DID they created in (1). For that, they need to take the issuer's decentralized identifier (DID) that they got from credential presentation and determine who it belongs to.














Let's personalize your content